Flags, Fun, and Fundamentals: A Beginner Guide to CTF
Beginner’s guide to CTF. Even a basic understanding of how CTFs function doesn't keep from encountering hurdles when it comes to getting started.

The hacker community has always been known for diversity of thought, expression and ideas, with everyone sharing unique talents and interests with others. From lifelong learners, to hobbyists, creating and tinkering with technology in different ways, the spectrum is broad, and while no community is perfect, the hacker community is often marked by a genuine spirit to learn and a willingness to help others grow.
It’s common to find people who want to get involved with the community in some way but find confusion in which direction to take. The sheer volume of resources can be overwhelming, resulting in choice overload, a phrase coined by psychologist Barry Schwartz, that simply means, when too many options exist, nothing gets chosen.
The goal of this guide is to provide a simple introduction to CTFs (Capture the Flag) competitions, because in my interactions with others, I have found it a topic that both fascinates and confuses people simultaneously. I have noticed even those with some familiarity still encounter hurdles.
Perhaps you have zero knowledge but want to learn what CTFs are about or haven't found the motivation. Maybe you’re interested but feeling apprehensive about performance, skills, starting points, or how to connect with others. Add a pinch of imposter syndrome and fear of judgement and it’s easy to find yourself stuck before ever starting.
No matter where you’re coming from, however, I hope this guide encourages you to explore what CTFs have to offer, push past your comfort zone and build the self-assurance to tackle challenges. If you're considering trying a CTF, curious about how they work, or just seeking beginner-friendly material, this guide is for you. My goal is to both inspire and serve as a helpful resource, and it is my sincere hope this post does that.
You may find that CTFs aren’t about rankings, or how great you are at something, rather challenging your own limits and capabilities instead.
- pirate.moo
It's Ancient History
The non-digital version of Capture the Flag is a game many of us are familiar with due to its common association with gym classes and summer camps around the world. While its exact origins lack a firm timeline or regional history, the game is believed to have originated many centuries ago as a military tactic and training tool used across various regions worldwide.

It wasn’t until 1860 that documented rules of the game were found however, thanks to a German gymnast name Wilhelm Lübeck in his manual Lehr - und Handbuch der deutschen Turnkunst. He referred to the game as Fahnenbarlauf, a reference that originated from a European variant known as Barlaufen played in both France and Germany.
This era also saw the importance of capturing flags on real battlefields during the U.S. Civil War, where Medals of Honor were awarded for such actions, including George W. Reed who received one in 1864, for capturing the flag of the 24th North Carolina Infantry.
Capturing enemy flags during this historical period wasn’t arbitrary, because thick gun smoke covered battlefields and made receiving commands incredibly difficult for soldiers. Officers tasked with flag carrying became focal points, indicating progress or retreat. Capturing such flags wasn’t about symbolism but disrupting enemy communication and morale.

The importance of this role often meant soldiers realized the disadvantage an enemy would have if they lost their flag carrier. The job of both bearing and attempting to take flags meant those soldiers often paid with their lives.
Reed, a soldier in the 11th Pennsylvania Volunteer Infantry (known as The Blood Eleventh for fighting in battles like Gettysburg), was working his way through the woods when he encountered a group of Rebels from the 24th North Carolina infantry, which included their flag carrier. After being captured, Reed warned the group of the danger they were in by pointing out their location in enemy territory and offered safe passage in exchange for surrender, to which they agreed.
While we enjoy capture the flag as a hobby today, in medieval times banners were often used by Kingdoms to mark territory and lead troops during war. The capturing of such banners was considered a great mark of triumph that demoralized the opposing side.
As times change, so do the methods and ways in which we do things. With the advancement of technology, the creation of hacking-based Capture the Flag competitions was born. The flag is no longer a piece of physical fabric, but hidden information contained in a vulnerable machine.
To Infinity and Beyond!
If you’ve been around the hacking or tech community for a while, you’ve probably heard someone mention DEFCON, one of the world’s largest hacking conventions. Held annually in Las Vegas, it takes place around the same time as the Black Hat conference.

DEFCON started in 1993 when Jeff Moss (The Dark Tangent), decided to host a going-away party for a friend who was moving. The name was inspired by the WarGames movie, which references the military term. What began as a small group of friends grew into an amazing conference packed with everything from talks, parties, and competitions to all things hacking and tech.
This also includes the DEFCON CTF, which started during DC4 in 1996 and is considered one of the most challenging competitions globally. The competition attracts top teams from across the globe who compete for the illustrious Black Badge, which provides free lifetime admission and recognition. It’s also one of the oldest currently running CTFs today.

While CTFs use automated scoring systems now, points were originally awarded at a judge’s discretion, which led to problems during the first few years of competition. However, CTF’s became much more streamlined when the team ghettohackers became the first organizers of the event, after an impressive three-year win streak at DC7, DC8, and DC9.
When ghettohackers stepped down, team Kenshoto took over. They brought a renewed emphasis on binary exploitation and introduced qualifiers to the CTF, before DDTEK (Diutinus Defense Technologies Corp. from sk3wl0fr00t) took the reins. The process of handing off who organizes the event every few years continues to this day.
You’ll find that CTFs run year-round with almost every major security conference, and many University programs holding competitions annually.
Famous Wins
Famous wins are a bit subjective, but teams like ghettohackers and Kenshoto that date back to the beginning of CTF hacking in the late 90’s and early 2000s are historically significant because it showcases how the game evolved over time. In DC16 for example, DARPA’s CGC (Cyber Grand Challenge) was held at the con, and team Mayhem marked the first time an AI system won the CTF and earned a Black Badge.
The Carnegie Mellon University team, Plaid Parliament of Pwning (PPP) dominated DC CTF for over a decade with record-breaking consistency, which included some incredibly hard challenges. While Pwn2Own focuses on zero-days rather than traditional CTF, some wins are noteworthy, like Charlie Miller’s repeatedly various Apple Safari vulnerabilities, VUPEN’s seven-year success streak and most recently Sina Kheirkhah’s first-ever win in AI by exploiting Chroma. The most famous win of all, however, is the one you gain from learning something new.
CTF Types
In the original version of Capture the Flag, the game is played by dividing a field into two territories, each with a team assigned. Both teams have a flag, or designated item they must protect from the opposing side. Players take on offensive roles by attempting to enter enemy territory to retrieve the opposing flag and defensive roles by thwarting retrieval attempts from the enemy. The team that can bring the enemy flag into their base without being tagged wins.

The digital version of CTF mirrors this concept, but just as the historical game evolved with variations, so did CTF hacking. In CTF hacking games, flags are digital strings hidden within vulnerable machines, challenges, or services that players must locate, solve or put together. These flags can be found in various locations like different user and administrative accounts, running services, by either fixing or exploiting code, or by solving problems like cryptographic puzzles.
The way a CTF is played, how it is organized, and the rules involved are influenced by the type of CTF it is. While Jeopardy and Attack & Defense are the most frequently used formats, others exist, including Bulluminar, and KOTH (King of the Hill). Although some CTFs are not structured competitions, platforms like Hack the Box and TryHackMe fit into the same genre because they follow the principles of flag capture. Instead, users are targeting vulnerable machines and challenges individually, or as part of a learning path.
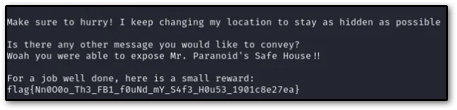
Flags tend to follow a specific format outlined in competition rules, so it’s always important to read through them for good measure. The core of a flag is usually placed within curly braces { }, while the name of the CTF or event is placed outside them. Flag text is usually references a challenge in some way. Below is an example of how flags look:
CTFNAME{th1s_fl4g_w4s_c4ptur3d}
Flag submission is typically done by pasting flag contents into a CTF challenge interface that becomes available after the CTF starts. You can find lists of challenges available by category and competitions range from hours to days, or longer. This is always dependent on the event, so it’s important to submit flags quickly, so you can work on other challenges.
CTF subjects are typically divided into these categories:
- Web: Finding/exploiting vulnerabilities in web applications
- Crypto: Encryption, decryption, hashing algorithms, and cryptanalysis
- Pwn (Binary): Finding/exploiting vulnerabilities in compiled programs
- Reverse Engineering (RE): Analyzing compiled or obfuscated code to understand functionality
- Forensics: Analyzing digital evidence, network traffic, or mobile devices
- Miscellaneous: A catch-all for challenges that don't fit into other categories
- Open-Source Intelligence (OSINT): Analyzing publicly available information
- Hardware: Finding/exploiting vulnerabilities in physical devices
When we reference someone obtaining a First Blood (or second/third blood), we are saying they were the first person or team to solve a particular challenge: In some cases, this could mean bonus points, or recognition from peers for solving something seen as extremely difficult. In others, it could refer to the speed in which they were able to figure out the challenge.
A good rule of thumb is to note how many solves a particular challenge has. It’s good to ask yourself the following when competing:
- Were they able to solve this challenge quickly?
- How many teams were able to solve this challenge?
The answers to these questions can help us understand the level of difficulty assigned to a particular challenge or provide us with a timeline in which a flag can be obtained.
Jeopardy
Jeopardy is probably the most common CTF format you’ll encounter because it’s designed to cover a broad range of categories. Each category has multiple challenges, presenting a task that needs to be solved, and challenges are allotted to a certain amount of points for doing so, based on perceived difficulty (some CTFs will tell you the difficulty level). Easier challenges provide less points, while more difficult ones give more. A lot of platforms use dynamic scoring systems however, so if no one solves a particular challenge, its point value may increase. Similarly, if everyone solves a certain challenge, the point value may be decreased.
Attack and Defense
Another common platform popular with universities is Attack & Defense, the most notable being CCDC (National Collegiate Cyber Defense Competition). Each team receives a topology (network map) of a specific network environment, or “Gamebox”. Attackers need to discover vulnerabilities on the services running and exploit as many as possible to obtain flags, while defenders need to keep those services running, patch issues, and mitigate vulnerabilities to either stop losing or gain points. Since these competitions tend to be longer, there are breaks where attacks can’t be done and services change. Both teams begin with the same point values and organizers update which service contains a flag. If attackers obtain the flag, the opposing team loses points, but if the team keeps services running, defenders receive points. Obtaining root on a Gamebox is generally forbidden and can result in a permanent ban.
Belluminar: War Sharing
The term Belluminar is a compound word, from the Latin word war (Bellum) and seminar. This game format started in 2015 in South Korea by POC SECURITY and was introduced in China the next year during the World Hacking Masters Challenge (WCTF). You may not have heard of it because only invited teams may participate, with each team showcasing their ability in both attack and defense, by attacking the challenges the opposing team creates. The invited teams must each submit two challenges before the competition and have 12 weeks to prepare them, as it accounts for 30% of a team’s total score.
The first challenge must be created using Linux, while the second has no restrictions. Both teams must draw for their challenge type and each team must submit full documentation about the challenge, including a write-up with solutions for what they create. After challenge creation, organizers test the challenges and code before placing them on the platform and teams can request to solve their competitor’s challenges. Ranking is based on points earned by solving and creating challenges and after the game, each team prepares a presentation with their thought process, solutions and knowledge to the opposing team. At the same time, they answer all forms of questions from both judges and competitors, who later rank the challenges. Below is a breakdown of how these types of CTFs are scored:
Creating challenges (30%):
- 50% level of detail, completion, submission time/50% from solved challenges
- The number of teams that solved the challenge
- The number of teams expected to solve the challenge
Score from solving challenges (60%)
Score from sharing (10%): Based on content during the sharing meeting voted on by players/judges
King of the Hill (KOTH)
CTF hacking competitions aren’t the only place you see King of the Hill battles, with popular FPS games like Halo featuring them in their lineup in the past. TryHackMe is probably the best-known site for hosting KOTH competitions however. This variation deals with maintaining control over a digital asset/system for as long as possible. The HILL contains a specific file or tagged item with the flag, and teams must keep a service, file, or network running with accessibility while maintaining control of the HILL. The longer a team maintains control, the more points they accumulate, which are tallied after the pre-allotted game time is up. At the same time, opposing teams try to gain and retain control of the hill. After scores are tallied, the team with the most points at the end wins. Variations include games where multiple and dynamic hills exist and change over time. Making the hill unavailable isn’t allowed.
Wargames/Platforms
Some learning and hacking platforms use a CTF style format like Hack the Box and TryHackMe, but others exist like picoCTF, PentesterLab, Proving Grounds, Parrot-CTFs, and VulnHub to name a few. Some of the services are free, but many of these platforms typically follow a tiered subscription model to maintain access.
Women and CTF
As a woman, it’s hard for me not to bring up this topic, as it’s so often misunderstood. There are CTFs geared towards underrepresented groups that try to encourage participation, because play rates are significantly lower. Women are one such group. There isn’t an exact reason, but it’s believed a lack of representation, misconceptions, and general misunderstandings all play a role on why less women compete. Another reason could be related to the constant pressure some women might feel under within technical fields to ‘always perform perfectly’ without showing the learning process for fears they could be attacked for not knowing something on places like social media. Stereotyping, imposter syndrome and a lack of information all contribute to this multifaceted issue, but diverse teams are good because they bring wider ranges of approaches and differences to problem solving and creative thinking approaches.
Dedicated organizations and groups like WiCyS (Women in CyberSecurity), WSC (Women’s Society of Cyberjutsu), TDI (The Diana Initiative), and WISP (Women in Security and Privacy) actively promote and support the involvement of more women in all areas of tech, including the CTF circuit. Workshops, mentorships, and networking opportunities help to encourage involvement and representation.

Events like Wicked6, the Power of XX in Korea, and the Kunoichi Games in Japan, along with localized competitions and CTF teams like the US Women’s Cyber Team, help provide a supportive atmosphere that encourages women to learn, compete and build confidence without pressure. As someone who has competed in such events, I can tell you they’re not only a lot of fun, but a great place to meet others with similar interests in CTF!
Please keep in mind not all events are exclusively for women and some events are for other underrepresented groups in tech. Mixed participation is allowed depending on the CTF.
Accessing Resources
Web
The web category primarily deals with finding flags in various web application vulnerabilities. These bugs range from well-known issues like SQL injections, Cross-Site Scripting (XSS) and Cross-Site Request Forgery (CSRF), to problems with upload and inclusion mechanisms, command injection, path traversals and bugs in scripting languages like PHP.
It’s an exhaustive list, but my goal isn’t to explain every issue; there are amazing resources already dedicated to that. I will, however, provide some of those resources, and explain ways that can make your learning experience more efficient.
The first resource that always comes to mind is the PortSwigger Web Academy. It allows you to not only learn material but do so with labs that contain all kinds of web vulnerabilities.
Wargame platforms like Hack the Box, TryHackMe and picoCTF all have different challenges categorized by topic and search features allow you to narrow down what you’re looking for when practicing. Not only that, but many of these vulnerabilities also apply in real-world testing scenarios. After signing up on a wargame platform like Hack the Box, you’ll get a dashboard like the screenshot below:
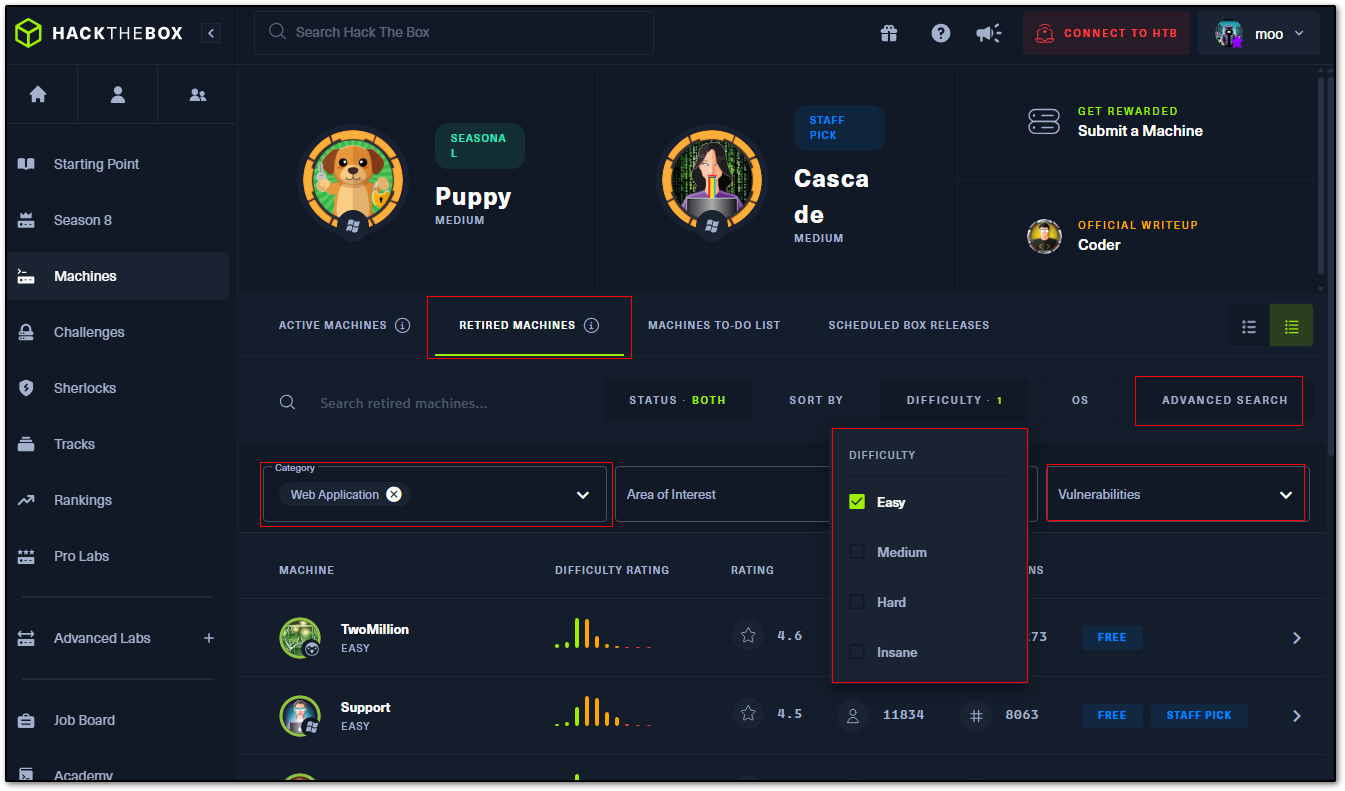
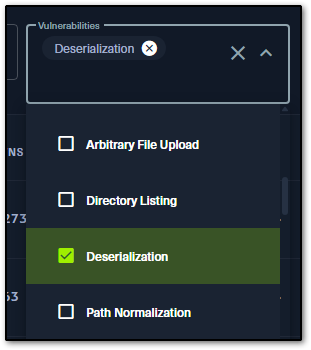
Clicking on retired machines indicates the listed machines aren’t active and won’t give any points, but that doesn’t diminish value. For people who are new, they can be great because they often have accompanying write-ups and video content. The Advanced Search feature provides specific filtering, and Category pinpoints the exact vulnerability you want to look at in the Vulnerabilities drop down. The list of machines dynamically adjusts. As you can see, I’ve chosen deserialization. Awesome!
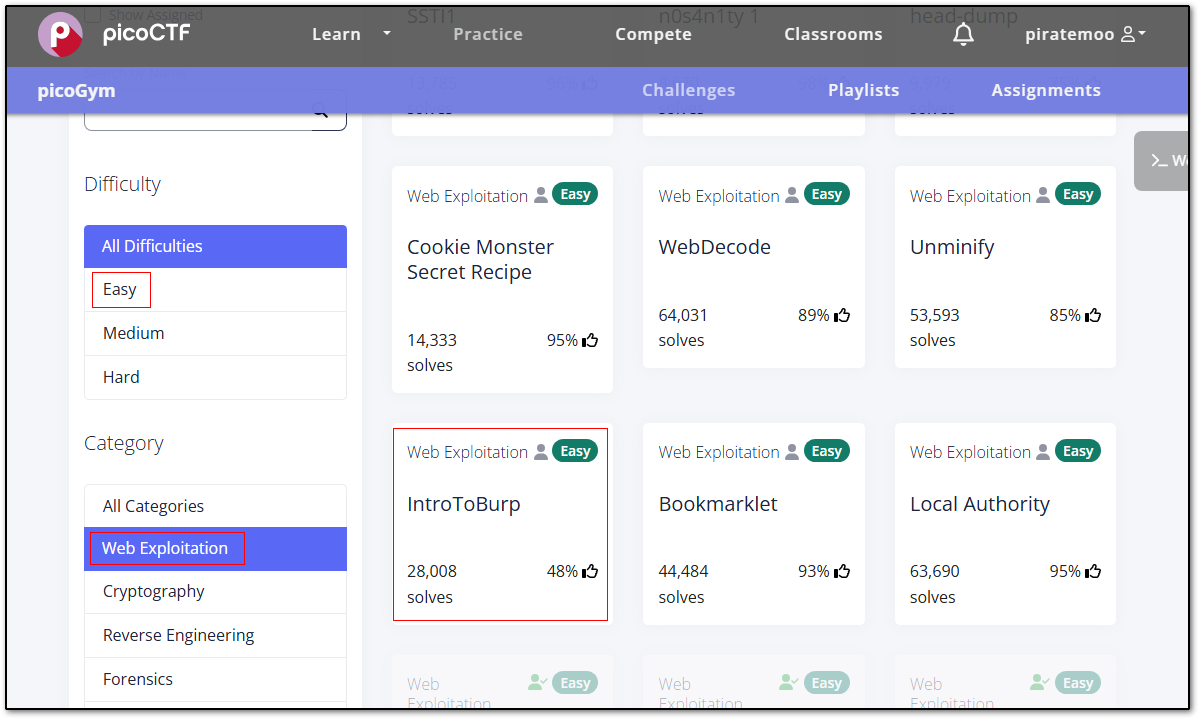
If I click on a machine, a new dashboard appears, offering options like starting the machine and a walkthrough tab. Within this tab, I can read the Official HTB Walkthrough or watch a YouTube video on the machine by ippsec. Sweet! Most Wargame sites operate similarly. Here we see a similar example using picoCTF
Here we see a similar example using picoCTF
Other resources include TryHackMe’s Web Fundamentals learning path, the OWASP Top 10, OWASP Juice Shop and Awesome Lists on GitHub. Here’s one for web: Awesome Web Security
You will learn a lot from labs but learning to use Burp Suite is a must for web hacking. Good enumeration can also make or break a challenge, so utilizing Kali (or your preferred distribution) with tools like dirbuster, feroxbuster, ffuf, sublist3r, and subfinder are a good idea. The same goes for having a thorough understanding of how to work nmap with NSE scripts.
You can always check the source code of a page with view-source:https://URL to see how it was made and get a feel for how it was set up. F12 and developer mode in browsers are your friend as shown in the screenshot below.
The /robots.txt file can provide a little information because they’re used to control how search engine crawlers access a site. Extensions like Wappalyzer are great for understanding what’s running in the background too.
Crypto
Did you know cryptography is like 3,000 years old? It's derived from the root word kryptos, meaning hidden and grafo, meaning write. It relates to the study of message secrecy and deciphering writings or ciphers. One such application was using an ancient Greek cylinder tool called a scytale (ancient Greek for baton or cylinder). It was used by Greeks to encrypt messages produced by different cipher text. First mentioned in the 7th century BCE, the writer would wrap parchment around a rod, while the recipient used a rod of the same diameter to decipher it.

It's common to encounter basic ciphers such as Caesar, Atbash, Affine, and ROT13 in introductory challenges. CyberChef is a widely recommended tool in the CTF community because it helps in tackling introductory challenges and allows beginners to focus on understanding them. For challenges involving hash functions or password cracking, Hashcat and John the Ripper are the go-to.
When you’re looking at challenge, reading the text can be extremely important in finding clues about how to find the solution. There could be ciphertext, or files you’re provided with, or keywords like XOR, AES, DES, RSA, or ECC that can give you an idea of what algorithm is being used. If there’s a file, can you check the source code and use tools like strings, file, and binwalk to gain more information?
More advanced challenges like ones that include number theory (RSA/ECC), are where math software and libraries become super important. Python’s cryptography and gmpy2 libraries can be useful.
Sites like dCode.fr offer a collection of solvers and site sites for breaking substitution ciphers like QuipQuip come in handy. Tools like xortool, hash-identifier, Tunnels Up and pwntools are also useful.
If you're just looking for platforms to deepen your understanding, TryHackMe offers a Cryptography 101 room designed for beginners. For hands-on practice, try challenge sites like CryptoHack, Cryptopals, Root-Me, and MysteryTwister.
Pwn (Binary)
Pwn challenges revolve around exploiting binary executables to gain control of execution flow and read flags, which is often hidden within a system/process. It typically requires reverse engineering to understand how it functions and to identify flaws like buffer overflows and format string bugs. Buffer overflows, for example, happen when a program tries to write data beyond boundaries of a fixed-size buffer. The extra data spills into other memory regions, overwriting instructions. There are two primary types of (stack and heap), based on where the buffer resides.
When we’re looking at these types of challenges, it’s important to understand the architecture involved (is it x86 or x64?). Tools like GDB, IDA Pro, Ghidra, WinDbg, radare2 and Binary Ninja among others can be used to convert binary into assembly. We also want to know if there are any protections like stack canaries, ASLR, or NX in place, since it affects exploitation and whether things like a ROP chain/gadget might be used.
When trying to piece together what’s happening though, looking at functions that are known to be notorious for issues like sprintf, memcpy, or strcpy is a good idea. Players can see if they can use format specifiers to write to arbitrary memory locations.
If you find this topic challenging, there are a lot of excellent resources available to help like pwn.college which also has a YouTube Series on the subject. Sites like ROP Emporium, Hoppersroppers Roadmap and Intro to SW Exploits are great but Sam Bowne: Exploit Development for Beginners is still great too. Another one, xor pd: Assembly Language Adventures is a nice class on Udemy that really explains a lot of core concepts well. If you’re looking for an academy course on the subject, check Hack the Box: Stack Based Buffer Overflows on Linux x86. Pwntable is also a pretty good challenge practice site dedicated to these kinds of vulnerabilities.
Forensics
Forensics challenges involve analyzing digital evidence to uncover information. This can be done in a few ways like creating disk images, creating memory dumps, analyzing PCAPs for network traffic, and looking through log files. Sometimes images can have hidden data, known as steganography and we have to analyze the image in order to find it. The same is true for things like compressed files.
Players try to find the kind of file being dealt with utilizing tools like file, strings and binwalk, see if there needs to be any file carving with foremost or scalpel, or sift through log files using grep and awk. Tools like exiftool and sites like Aperisolve are great for finding EXIF data if there’s a possibility an image may be encoded. We can also use tools like Autopsy to analyze drives or media and HxD if hex editing is needed. For mobile forensics, tools like a plist editor, Android Studio/ADB, jadx, or MobSF can also be useful.
Open-Source Intelligence (OSINT)
OSINT challenges focus on gathering publicly available information to solve a puzzle, find a flag, or uncover specific details about a target. When dealing with these types of challenges, it’s important to pay attention to every detail provided and to determine whether it can be perceived in a specific way.
When looking at these types of challenges, you want to see if any information about names, locations, or messages are used. Google Dorking and using the right operators can be exceptionally strong here, but if you’re newer to that, try advanced google search. If checking through social media platforms, tools like Sherlock can be extremely useful in connecting account names. Reverse image searching and checking files with string is also useful.
Pwn2Own

Pwn2Own, a widely known hacking competition takes place throughout the year at various conferences. Organized by the Zero Day Initiative (ZDI) from Trend Micro, it was first held in 2007 at CanSecWest, by Dragos Ruiu in response to concerns in OS X and it involved hacking MacBook Pros.
Researchers from around the globe try to exploit unknown vulnerabilities, or zero-days in common software and hardware. Players demonstrate new working exploits in exchange for cash prizes and Master of Pwn points. The team or researcher with the most points gets crowned “Master of Pwn” and receives a special jacket, along with cash prizes from ZDI purchasing the vulnerability for private disclosure to the affected vendor. This allows for a 90-day patch and fix window and responsible disclosure. To date, some of the largest prize pools have hit over $1 million dollars!
Before the event, ZDI announces the categories and versions of targets that will be used, but there are limited attempts and a timeline in which researchers must find something. Generally, the exploits also must achieve code execution with little to no interaction, making the bar for entry relatively high.
Strategies for success
If you’re going into your first CTF, here are a few tips and tricks to help the process end up a bit smoother, but these aren’t like solid rules. They’re things I’ve learned through my own journey that I hope will help others.
First and foremost, take the time to understand the time zone the competition is in and convert those hours into your local time. I cannot tell you how many times I and others have made this mistake, only to find that a CTF started a few hours back, or I screwed up the date entirely. Also ensure you know how LONG the CTF is. This will help you allocate your time more wisely.
Also make sure that you know exactly what you’re signing up for: What type of CTF format is it (Jeopardy, Attack & Defense, ETC) and ensure that you know the level of DIFFICULTY. If you are brand new to CTFs, you don’t want to sign up for something way more advanced. That tends to make people feel awful and causes morale loss.
Make sure any virtual machines are setup BEFORE the CTF starts and that all the tools you will be using are already on and updated. I cannot stress how many people I’ve seen kill hours on time because of this. Also be sure that you HAVE any team passwords available BEFORE the CTF starts.
Maintaining focus and preventing burnout are key throughout a CTF. That means you should schedule regular breaks, such as a 15-minute pause every hour or two, and stay well-hydrated. That will help keep you focused and not cause exhaustion. I know A LOT of people tend to break this rule (me included) and it causes nothing but suffering. Trust me. I do get that it’s easy to get sucked into a challenge and forget this but set a phone or watch alarm if you must.
This same rule also applies when you’re faced with a difficult challenge that you’re not making any progress on. If you get stuck on a challenge for too long with no progress, skip it for a while and move onto another challenge. I cannot tell you how many times I was able to solve the new challenge I attempted quickly, and then when I returned to the problem I was stuck on, coming in fresh created the change I needed to solve it.
If you are on a team, ensure that there are some people assigned to tackle more difficult challenges at the start. Since these take longer to solve, splitting a team this way can help them focus on a higher point flag, and others who are not as experienced can work on the more low-hanging fruit flags available.
Note-taking is HUGE. Take notes and screenshots AS YOU GO so you can document how you solved a problem later, or if you create a write-up, which yes, you want to do irrespective of your score. This will give you more freedom later, allow you to reinforce what you did and learned and see how you can do it better next time. I recommend Obsidian for note taking and Greenshot for screenshots. If your team has a tool like CTFNote, this can also be used.
Have a platform like Discord or Slack that you can engage the CTF and your teammates with. Sometimes challenges go down, or correct flags aren’t being accepted. You want to be able to have a ticket going if this is the case. You also want to engage and communicate with your team, so multiple people aren’t working on a solved challenge.
If you find yourself without a team, don't worry! If you want to find people, many CTFs have a dedicated Discord where people look to form/join teams right before and during the competition.
Make sure to read the write-ups from the previous year of that particular CTF. It could help provide an idea of what kind of challenges you might be faced with. Platforms like CTFTime keep write-ups logged for every CTF they can. Check the write-ups for the answers to problems you were stuck on as well after the CTF.
Do NOT provide hints, clues, or flags to anyone not on your team: This can get you permanently banned from competing in the future.
Lastly, at the end of the day, it’s just a game: Be a good sport and be kind to people on your team and other competitors. Respect can go a long way.
Mindset
There are a lot of mental traps one can have when considering playing for the first time, so let’s talk about a few of the common ones I’ve seen people express. A frequent one I encounter from people interested in learning, or working in tech is imposter syndrome, or when a person doubts their skills and feels like a ‘fraud’ in some way. It’s perfectly normal to experience these emotions at some point, but it’s important to remember that participating in CTFs, like any new endeavor, requires time, research, energy, practice and patience!
It’s OK to feel unprepared or confused when starting out. Everyone experiences these feelings at some point, but you’re not expected to know everything immediately and there is a learning curve. Remember, the goal isn’t to win but embrace new experiences.
You do not HAVE be a rockstar to participate in challenges. That tends to be a self-limiting trap that can cause paralysis from learning. Everyone starts somewhere and there are beginner challenges in most CTFs. You’ll learn a lot by doing, not just knowing. You also do not have to solve every challenge on the board and chances are good that you won’t because they’re geared for different difficulties.
It’s also common to get fixated on a particular way of trying to solve something, even when it might not work. In gaming we call that tunnel vision – you’re so focused on one aspect of the game, that you don’t realize you’re failing mechanics elsewhere. CTFs often contain what are known as rabbit holes so challenges may look like they should be solved a certain way, when they aren’t.
Not scoring points doesn’t mean you’re doing bad. The act of attempting to play and figure out challenges is a learning process. Maybe you’re helping your team by handling the enumerations for various challenges. The point is that failing to solve something isn’t a waste of effort. You can always read the write-ups people post with answers after the CTF to gain insight.
Social media write-ups and videos tend to present a very polished look at challenges and the effort involved. Note that these are typically the result of extensive failure, learning, experimentation, exploration and research. The actual timeline for understanding and solving some challenges is significantly longer than depicted. While CTFs have time limits, challenges can sometimes take hours, days, weeks, or even months to really grasp and write-ups/videos rarely represent that accurately.
You do not have to compete with a team if you do not want to for many CTFs. While some competitions do mandate a certain number of players, there are plenty that don’t. Engaging in Discord or Slack with the event will allow chances meet others. There are almost always people looking for others to play with during events.
The biggest thing to remember is that taking the initial step means moving in a direction. If you don’t take steps, you’ll never get to where you want to go!
Resources
Create your own CTF
Ultimately, this posts aims to serve as a reminder that there are a lot of intricacies everywhere and CTFs are no exception. I sincerely hope this guide helped in some form or another and hope to see you playing soon!
A true flag is torn from the soul of the people.
