PancakesCon CTF 2022

Authors: piratemoo/azuleonyx/sh4na/whateverwally
PancakesCon is a free virtual cybersecurity conference run by @hacks4pancakes as a way for speakers to discuss not only cybersecurity, but NON-IT related hobbies and interests, which in this day and age is a complete breath of needed fresh air!
Along with an amazing speaker line-up this year, @TabbySable, and @ryancdotorg put on an amazing CTF event. For PancakesCon, I opened the Space Cows CTF team to all new players who wanted to get their hands dirty, and what an amazing response and turn-out! With a tie for 2nd place, Space Cows went above and beyond expectation to get it done!
The only disadvantage to the CTF was the amount of time we had to grab as many challenges as possible, as PancakesCon is a 1 day event. :}
The challenges were grouped into three main categories:
- Network Enumeration
- Pwn
- Crackme
Crackme:
Nur Geträumt
Getting some of the crackme's to run properly was a bit of a challenge in itself, but once you got Nur Geträumt to run, you were given the following statement:
Hello there.
I'm from the DISTANT FUTURE, where normal computers run at 2-4 GHz and 16 GB is considered a medium amount of RAM. That's right; we have more RAM than you have hard drive space.
The good news:
Unicode really seems to have worked, for the most part. We even have characters for clown faces and smiling piles of poo. The Mac is still a pretty big deal, and can still read this program (but hasn't been able to run it for a while).
Nearly all computers in the world are connected together through a network called the Internet. Depending on when you read this, you may have heard of it. Don't t get rid of MacTCP just yet.
The bad news:
Nearly all computers in the world are connected together through a network called the Internet. This has made a lot of people very angry and been widely regarded as a bad move. Despite having 16 GB of RAM, Microsoft Word still takes up roughly half of it.
Anyway, because in the future we're stuck at home due to a worldwide pandemic (no, not the Internet, there is ANOTHER one), we had a competition for finding fun things in computer programs. I've hidden a flag in this program, but it's not going to be all that easy to find just with ResEdit. You'll probably need to interact with the program a bit.
Here's your first hint: you'll probably have to wait until 1997 to figure this one out, but much after 1997 and the Internet can probably help you.
Have fun, and enjoy your PANCAKES{That's another hint, but this isn't the flag}!
- Dave, @6502_ftw, January 2022
% Flag string (try viewing in hex)While Shana poked around with the mini Mac, we searched around for possible clues to what album was being discussed. It was important to translate Nur Geträumt to "Just a Dream" in English. We discovered that Nelly had a single called "It was all a dream", which came out in 2010 and was clearly not what we were looking for, but was great for a good laugh:

Doing a little more research we discovered that this song "Just A Dream" was created by Hate Squad on the album Pzyco! circa 1997.

I have included Shana's amazing write-up of these challenges, which can be found here and pasted below: https://blog.worldofcoding.com/blog/pancakescon2022-ctf-writeup/
The challenge description told us that the file was “a 68k Mac application on an 800k floppy disk image which can be used on any emulator which supports them. The image runs well under Mini vMac using any System 7 base operating system.”
To get our little challenge to actually run, I’d have to go figure out what a Mini vMac emulator is and how to run System 7 on it. The Getting Started docs were helpful, but unfortunately these things bitrot faster than you can say “bitrot”, and while I could download the base emulator and images of the different OS versions just fine, the tools to extract the actual runnable disk images don’t work anymore.
You see, while System 6 images are distributed inside binary packages with extension sea.bin and the provided extractor tool run just fine on these, System 7 is distributed in a different file format of extension smi.bin. Like tar.gz, these are double packed containers, an smi or sea file inside a bin. MacOS can unpack bin files just fine, but it seems that the code that can handle smi files is long gone, and the sea unpacker can’t handle smi.
Given that our challenge file is made to run on System 7, this was quite the issue for me, and it took me almost two hours to get it running properly. In the end, a lot of googling produced a blog post where someone went through the steps for doing it, with provided links for pre-extracted disk images of System 7.
Chasing clues
While going through this exercise, I poked around inside the provided challenge file, and found a few interesting strings in it (seen above)
This sent the team on a bit of a chase down memory lane, trying to figure out what “album” this could mean. Nur Geträumt translates to “Just a Dream” in English, and we discovered that Nelly had a single in 2010 that was called “It was all a dream”. Could this be relevant?
apiratemoo also discovered a song called “Just a Dream” was created by Hate Squad on the album Pzyco! circa 1997. Another clue??
It runs!!
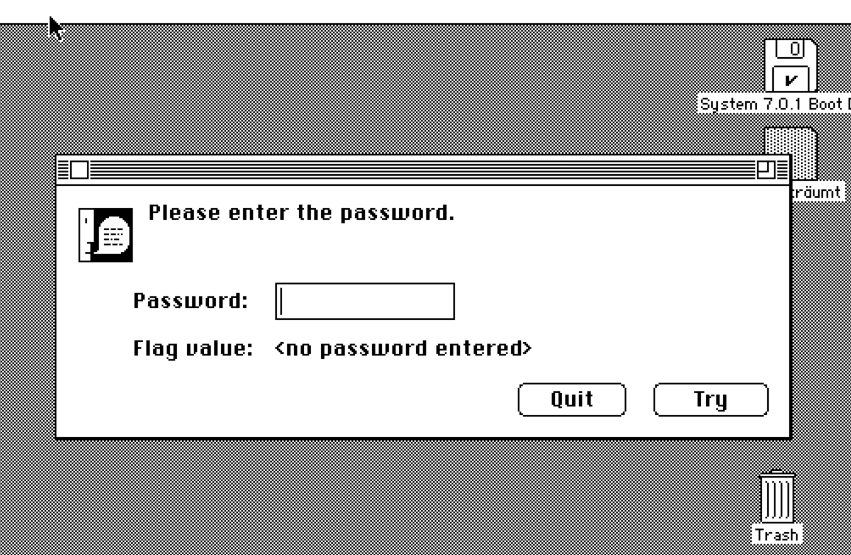
We get a prompt (a multiline prompt, even!) and we need to enter a password. Just hitting Try without anything in the input returned a short series of characters, entering anything else returned gibberish - but always the same length of gibberish, suspiciously long enough to be a flag. A Clue!
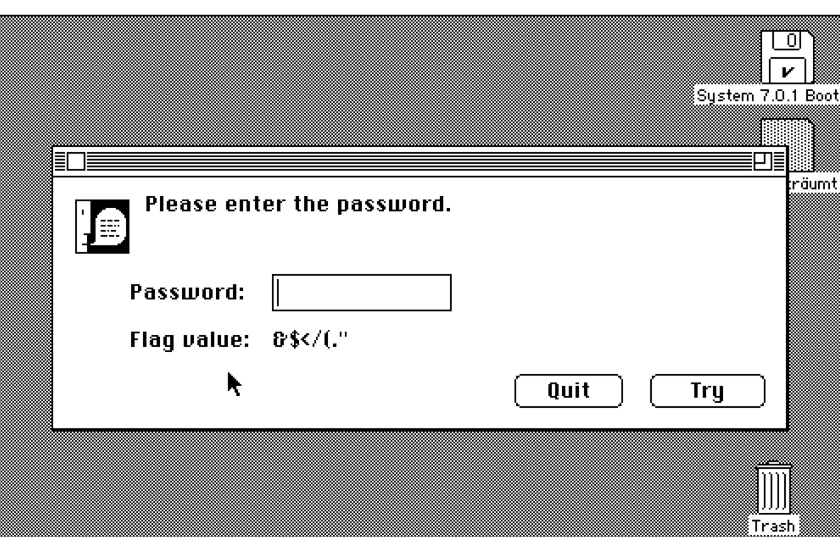
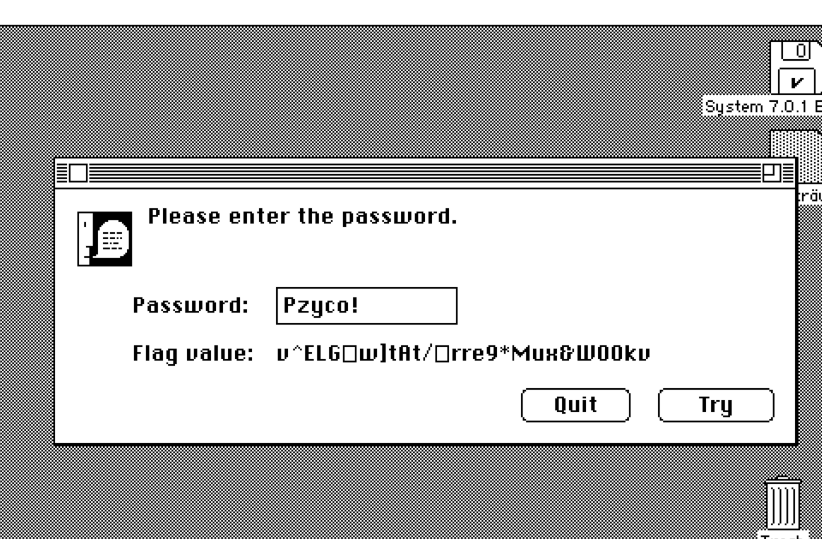
We tried different inputs from the band and album names we found, but nothing worked. Then, I entered PANCAKES - because we know flags in this CTF are always of the format PANCAKES{something in there}, trying the known parts of the flag might reveal something about the underlying encoding - and noticed that the result started with characters that formed a word, and that word had the same length as the flag prefix - a clue?
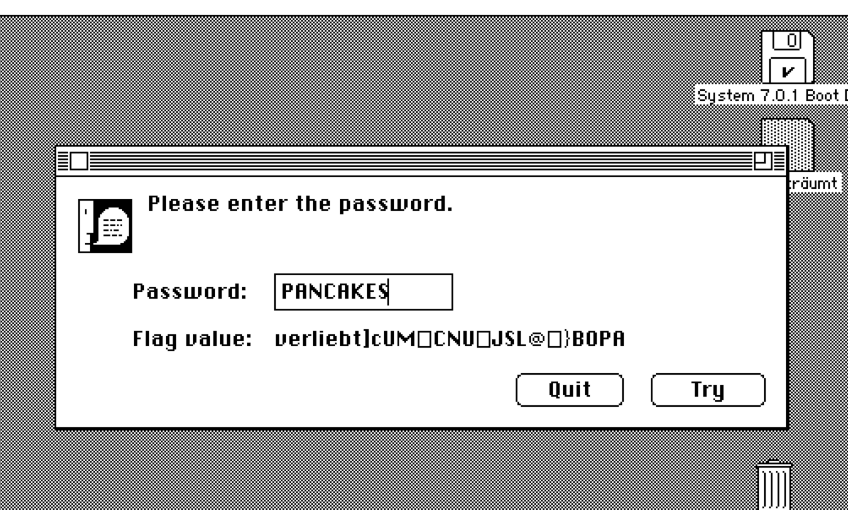
Someone (I was freaking out and didn’t catch who it was) suggested alternating the case of the input, so I tried PaNcAkEs and the result mirrored the case alternation with that same german word - Capital C Clue! Following the logic, if input PANCAKES gives me output verliebt, input verliebt gives me…

xorro
xorro was an ELF file that requested a four character password to solve: It returned a string based on the information given (in short, there are 9999 possible password combinations here). You could have gone the brute forcing route, but people used strings to help them out here.
┌──(kali㉿3f9eb66ce263)-[/var/workspace]└─$ echo 'ABC' | ./xorroWhat is the password?invalid password size
┌──(kali㉿3f9eb66ce263)-[/var/workspace]└─$ echo 'ABCD' | ./xorroWhat is the password?RbFbChMry:D1A94:CaBn┌──(kali㉿3f9eb66ce263)-[/var/workspace]└─$ echo 'ABCDE' | ./xorroWhat is the password?invalid password sizezorshift
Just an interesting note that we found this emulator while looking through the 390 architecture found in zorshift.

Notes on Bootselfie
There is a fantastic write-up on this by echelon already, but Shana wanted to point out a few words:
If you didn't catch her write-up above please go to: https://blog.worldofcoding.com/blog/pancakescon2022-ctf-writeup/
Bootselfie is so much fun, and I still haven’t cracked it, so I’m not going to link to any spoilers until I figure it out!
The challenge file is identified as a DOS/MBR boot sector. Before anything else, a quick look into the binary reveals interesting strings:
We hope you're enjoying the PancakesCon 3 CTF! You were looking for a flag?
This floppy has one! Hold on, we're getting a phone call...
Ugh, the 90's called and asked for their stuff back.
Where were we? Oh, yes! The challenge!
Enter password:The intro blurb helpfully mentions several emulators that can potentially run it, and I found that qemu did the best job of it.
After creating a base DOS image with qemu-img create -f qcow msdos.disk 2M, I ran the image with qemu-system-i386 -hda msdos.disk -m 64 -L . -fda floppy.b574a828701f512ac5fd6399be8990e5ce2738e5c0f71d74665592228ef3baa2.img -boot a
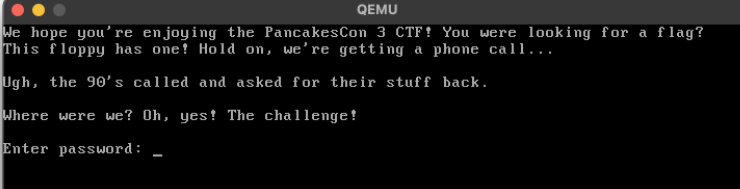
Turns out, the string is what shows up when the binary boots up.
Hitting any key outputs it, and when you input any 6 characters, the screen turns to snow.

Inputting the same set of 6 characters produces the same pattern of snow, and different sets produce different snow.
Peeking at code in IDA, one can see the code reading input one character at a time and echoing it to the screen until it reads 6 characters:
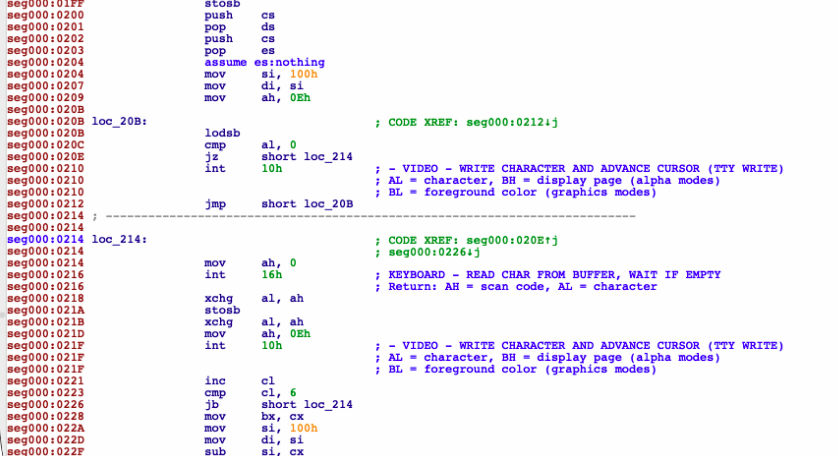
at which point it does… something…
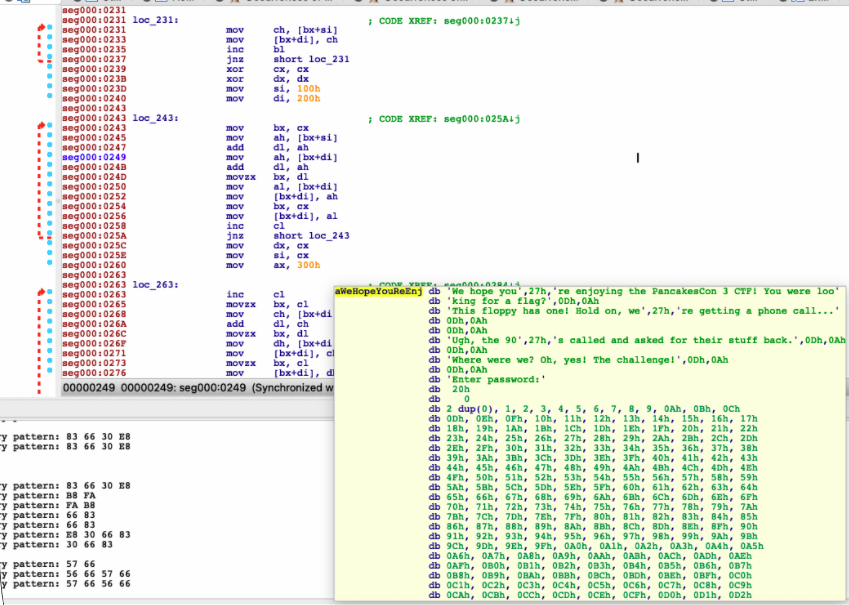
What that something is, I ran out of time to figure out!
Pwn
Pwn1 -
Write-up by Wallywhatever: https://twitter.com/whatever_wally
- User
The PancakesCon CTF was challenging, fun, and definitely had me working on things that I was not totally familiar with. This was my first CTF. It was a little daunting but my team was super supportive and we exceeded all my expectations. Here's a walkthrough on how I captured the pwn-1 user flag.
There were a lot of machines on the CTF network. Some of them were just decoys but one of the machines had an unusual service listed in the nmap scan:
map scan report for 198.51.100.63
Host is up, received user-set (0.051s latency).
Scanned at 2022-01-16 14:05:55 EST for 523s
Not shown: 997 closed tcp ports (conn-refused)
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 7.2p2 Ubuntu 4ubuntu2.4 (Ubuntu Linux; protocol 2.0)
[SNIP]
5432/tcp open postgresql syn-ack PostgreSQL DB 9.5.11 - 9.5.16
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=pwn-1.example.net
| Issuer: commonName=pwn-1.example.net
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
[SNIP]
31337/tcp open Elite? syn-ack
| fingerprint-strings:
| GenericLines, GetRequest, SIPOptions:
| !!!!!!!!!!!!!!!!!!!!!!!!!!
| Main Menu
| !!!!!!!!!!!!!!!!!!!!!!!!!!
| Welcome to The PancakesCon CTF user messaging system!
| Please log in to begin.
| List Users
| Selection:
[SNIP]Connecting to 198.51.100.63 31337 with netcat brought up the "PancakesCon CTF user messaging service."
On the main screen you could list what users existed or log in as a new or existing user (no passwords required). The following screen gave options for Send Message, Check Message, and Logoff.
The first thing I tried was some SQL Injection since there was also PostgreSQL running. Presumably thats the backend db for the messaging service. I didn't make any progress with this approach and soon moved on.
In the challenge listing there were also "source code" files: menu.m, message.m and user.m.
menu.m:
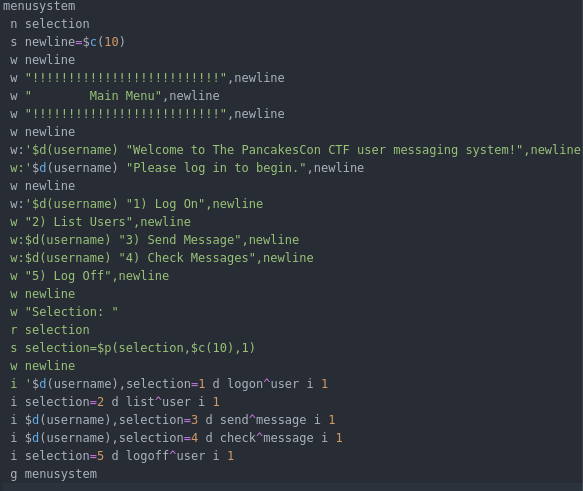
It seems to be a stripped down version of the source so that you can approximate the function of the program but not compile and debug it locally. I focused on the message sending system(message.m). Specifically where it reads the message in and assigns it in a string. I figured that this would be a good spot to attempt an overflow since there isn't a bounds check on the input.
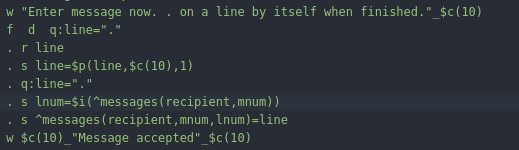
Just to do it quick and dirty I copy pasted a lot of "AAAAA..."s in. Nothing happened at first so I just added more until...
%GTM-E-REC2BIG, Record size (4095) is greater than maximum (4080) for region: DEFAULT,%GTM-I-GVIS, Global variable: ^messages("root",10,1)
At M source location send+20^messageGTM>Progress! We crashed and were now at some sort of prompt. Standard linux commands were not working though.
%GTM-E-CMD, Command expected but not found ^-----GTM>id
%GTM-E-INVCMD, Invalid command keyword encountered id ^-----GTM>Hmm...time to do some research on what the heck GTM is. Googling gtm on its own returned nothing useful but eventually I stumbled on this:
[GT.M Environment Setup]:
https://webcache.googleusercontent.com/search?q=cache:f2TgPpClr_4J:tinco.pair.com/bhaskar/gtm/doc/books/ao/UNIX_manual/ch03s01.html+&cd=4&hl=en&ct=clnk&gl=us
Okay so we're in some sort of debugging environment. The next goal is to figure out how to run system commands or to escape the debug jail. This involved reading a lot of the manual which took a while but the solution was simple.
Typing ZSystem; at the GTM prompt would drop to a shell. From there it was easy to get the user flag.
I think I may have inadvertently given other teams a hint on this because one of my teammates was able to get to the GTM prompt simply by checking a users messages.
I think that the overflowed message somehow saved and then would instantly fault when checked. I hadn't even considered that this was possible but in the future I'll be more mindful of that sort of thing. There wasn't an option to delete messages either so I couldn't have gone back and fixed it anyway.
This was my first CTF so the meta-game is something that I'm still learning. I also hadn't considered that I might want to do a write-up so I unfortunately don't have the screenshots I'd like to include.
This was a very fun and challenging CTF and I look forward to more in the future. Thanks to [Tabitha Sable] for creating the challenge and to the PancakeCon organizers. See you next year!
Pwn3
-User
Nmap scans from .51 output an interesting disallowed entry in robots.txt called fuel also labeled in http-title as FUEL CMS, which warranted further enumeration.
8000/tcp open http Apache httpd 2.4.18 ((Ubuntu))
| http-robots.txt: 1 disallowed entry
|_/fuel/
|_http-title: Welcome to FUEL CMS
|_http-open-proxy: Proxy might be redirecting requests
|_http-server-header: Apache/2.4.18 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelGithub provided the following gem and we were able to hardcode the ip:port to grab a shell on port 8000. flag.txt was in the base directory, but needed root.
Net Challenges:
Net-1:
"Find net-1 on the challenge network, study it carefully and determine the flag"
Grabbing the flag for net-1 consisted of doing exactly what the statement above requested: A more in-depth nmap scan would list it within the results, but you can also use tools like sslscan to do the same. :)
Nmap scan report for 198.51.100.240
Host is up (0.053s latency).
Not shown: 65532 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.8 (protocol 2.0)
| ssh-hostkey:
| 256 72:89:7e:27:da:97:ff:8e:e3:dd:dd:3e:0e:c7:72:80 (ECDSA)
|_ 256 0d:22:37:1169:74:75:28:71:2c:84:76:93:de:75 (ED25519)
80/tcp open http nginx
|http-title: Site doesn't have a title (text/html).
| http-robots.txt: 1 disallowed entry
|/flag.txt
443/tcp open ssl/http nginx
|_http-title: Site doesn't have a title (text/html).
| ssl-cert: Subject: commonName=198.51.100.240/organizationName=PancakesCon/stateOrProvinceName=IL/countryName=US
| Subject Alternative Name: DNS:198.51.100.240, DNS:example.net, DNS:net-1-flag:PANCAKES{cert_gave_it_away}
| Not valid before: 2022-01-15T21:24:56
|Not valid after: 2023-01-15T21:24:56
| http-robots.txt: 1 disallowed entry
|/flag.txt
[1:18 PM]
DNS:net-1-flag:PANCAKES{cert_gave_it_away}Net-2
SNMP enumeration did the trick here. You could run snmpwalk to pull community strings that contained the flag. onesixtyone within the flag is a tool reference for snmp enumeration. I didn't grab a screenshot, but you can find an example of one such tool below:
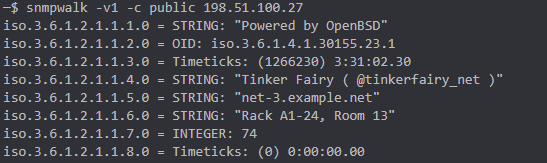
Net-6
Enumerating the SMB share that was open on the .13 address and utilizing crackmapexec with impacket pulled information along with the flag here:
SMB 198.51.100.13 445 NET-6 [*] Windows 6.1 Build 0 (name:NET-6) (domain:example.net) (signing:False) (SMBv1:False)└─$ crackmapexec smb 198.51.100.13 -u "" -p "" --shares
SMB 198.51.100.13 445 NET-6 [*] Windows 6.1 Build 0 (name:NET-6) (domain:example.net) (signing:False) (SMBv1:False)
SMB 198.51.100.13 445 NET-6 [+] example.net\:
SMB 198.51.100.13 445 NET-6 [+] Enumerated shares
SMB 198.51.100.13 445 NET-6 Share Permissions Remark
SMB 198.51.100.13 445 NET-6 ----- ----------- ------
SMB 198.51.100.13 445 NET-6 files READ
SMB 198.51.100.13 445 NET-6 IPC$ IPC Service (Samba Server)impacket-smbclient 198.51.100.13
Impacket v0.9.24 - Copyright 2021 SecureAuth Corporation
Type help for list of commands
# use files
# ls
drw-rw-rw- 0 Sun Jul 14 03:21:16 2019 .
drw-rw-rw- 0 Sun Jul 14 03:15:13 2019 ..
-rw-rw-rw- 31 Sat Jan 15 19:02:03 2022 flag.txt
# cat flag.txt
PANCAKES{network_segmentation}At the end of a long day filled with great talks, great fun and new friends, we called it an evening, went to take a break, and maybe ate some pancakes for dinner.
I look forward to seeing what PancakesCon has in store for next year!