Ladies of Space Cows: The Wicked6 US Cyber Range CTF Write-Up

On March 23rd and 24th, 2022, Wicked6, sponsored by many companies produced a special 24 hour global women's only CTF event virtually. For 24 hours, 1,000 women gathered together in Discord to play various CTF games and the ladies of Space Cows were no exception!

Information about the event can be found here: wicked6.com. Now onto the good stuff! The ladies of Space Cows comprised of 4 individuals, including myself (piratemoo), Faith XY, MeAsMe and Lady Acid and this write-up is comprised of our combined challenge solutions.
CRYPTOGRAPHY
Oh Caesar, my Caesar (5): This challenge consisted of a small Caesar Cipher that needed decoding: lfdphlvdzlfrqtxhuhg. I loaded up decode.fr/caesar-cipher and used the site to come up with icameisawiconquered. This website is great for handling various crypto related tasks, similar in form to Cyber Chef.
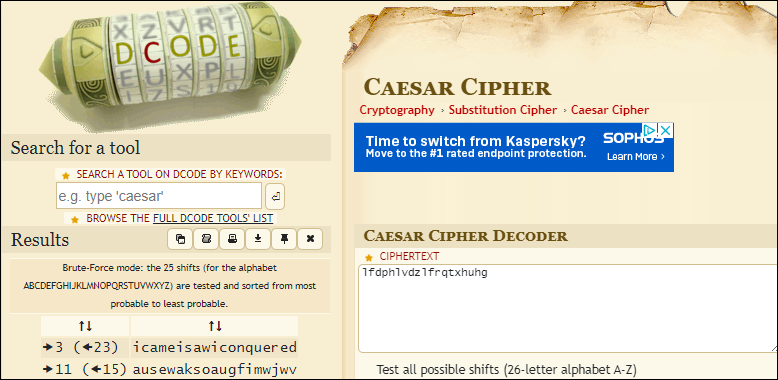
`dem Bones: There's a message here, I can feel it in my "bones"! (10) This challenge consisted of decoding a ROT13 cipher, GVONN BE ABG GVOVN, found in the following image, which came out to TIBIA OR NOT TIBIA, the flag.

Diffie-HELLman:
(p,g) = 799, 876)
A = 14
B = 99
To solve this one, you can simply go to irongeek.com/diffie-hellman.php or use a Diffie-Hellman exchange key calculator.
CyberDym: Missing Link: We're beta testing the blockchain for our new coin, CyberDym. There seems to be a missing link in the chain! Which link is missing? We just need the index value of the missing entry. Choose wisely! You only get 3 tries.
We are then presented with the following file (truncated because of length):
{
"index": 2,
"previous_hash": "d3bb3e83a9fa16d0adbce21747bcff8c457f8f13abebc1ca8bd853a823b96e14",
"proof": 102677,
"timestamp": 1549653717.627429,
"transactions": [
{
"amount": 1,
"recipient": "b92d4407f116411f8ee80cab4bed2cfe",
"sender": "0"
}
]
},
{
"index": 3,
"previous_hash": "03619d0c1684e89482628a12b67bc23ad6a30212cea36fde062df04d554468d5",
"proof": 13260,
"timestamp": 1549653717.6771493,
"transactions": [
{
"amount": 1,
"recipient": "b92d4407f116411f8ee80cab4bed2cfe",
"sender": "0"To solve this challenge, you needed to upload the file as a JSON and figure out which index was missing, which was block 3809.
CyberDym: Hacked! CyberDym is in production, but we've been hacked! Someone corrupted an early hash. I knew this private blockchain was a bad idea! Help us fix our chain before our Investors lose confidence and we go broke.
Can you find the corrupted hash? The flag is the last 10 characters of the correct replacement hash. Tries are limited to 20. For this challenge you are presented with 2 files.
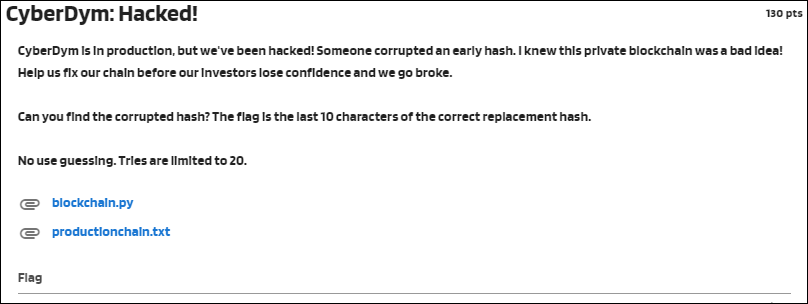
The following Python script was used to solve the challenge:
import json
import hashlib
def hash(block):
block_string = json.dumps(block, sort_keys=True).encode()
return hashlib.sha256(block_string).hexdigest()
f = open('productionchain.txt', 'r')
data = json.load(f)
prev = "1"
for i in data["chain"]:
if i["previous_hash"] != prev:
print(i["index"])
print(prev)
prev = hash(i)
print(hash(data["chain"][22]))
print(data["chain"][23])
f.close()NETWORKING
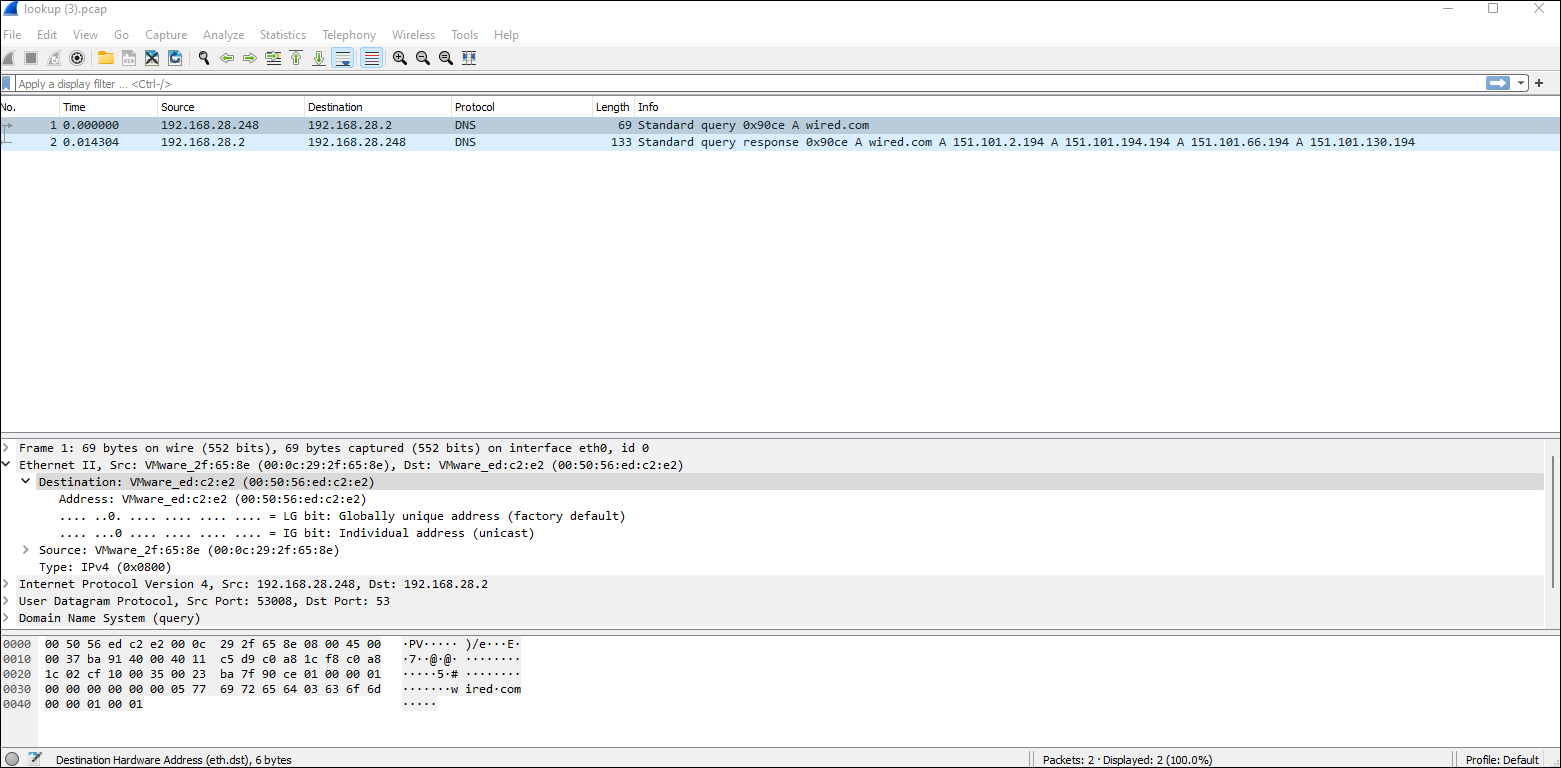
IP to Ethernet: In the attached packet capture file, what is the Ethernet (or MAC) address of the computer using IP address 192.168.28.248?
This was solved by analyzing the pcap provided with the address seen and then using 00:50:56:ed:c2:e2 for the answer.
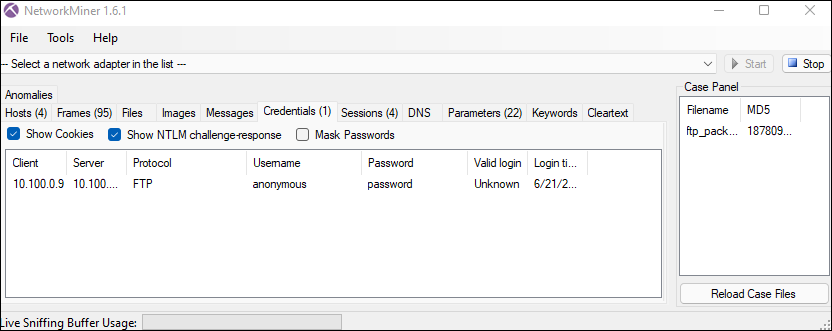
FTP: Who logged in? The following pcap is provided below:
To solve this challenge, I used an excellent tool called NetworkMinor to pull the credentials information fast. As we can see anonymous was the user who logged into FTP:
Morocco Mole: Sekrit Skwerl (sekritskwerl.com) has a flag hidden in his DNS records. Can you find it? To pull this information, I used a tool called dnsrecon and the flag was provided in the information below:
┌──(moo㉿earthcow)-[~/Desktop]
└─$ dnsrecon -d sekritskwerl.com
[*] std: Performing General Enumeration against: sekritskwerl.com...
[-] DNSSEC is not configured for sekritskwerl.com
[*] SOA ns21.domaincontrol.com 97.74.100.11
[*] SOA ns21.domaincontrol.com 2603:5:2141::b
[*] NS ns21.domaincontrol.com 97.74.100.11
[*] NS ns21.domaincontrol.com 2603:5:2141::b
[*] NS ns22.domaincontrol.com 173.201.68.11
[*] NS ns22.domaincontrol.com 2603:5:2241::b
[*] A sekritskwerl.com 45.55.189.36
[*] TXT sekritskwerl.com {flag:theresmoretodnsthanmeetstheeye}
[*] Enumerating SRV Records
[+] 0 Records FoundFile extraction! Do what the title says.
For this extraction, I used NetworkMiner again over Wireshark as it pulls the information I need quickly. I simply loaded the pcap, right clicked on the Files tab and opened the file to reveal the flag:
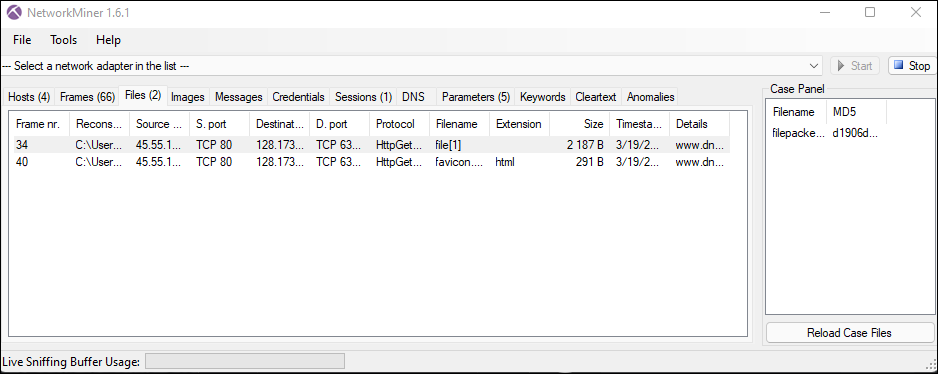
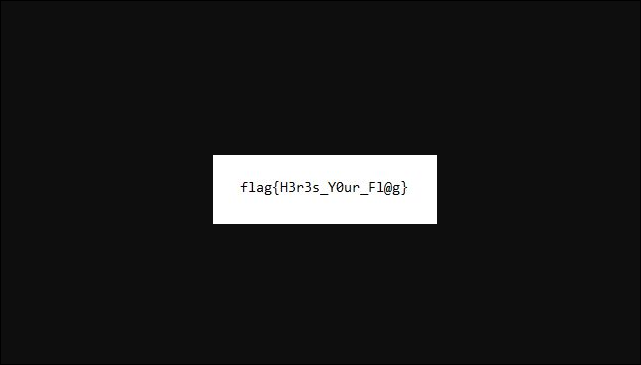
Where's Waldo...or rather, Holly? Street and number are fine. NOTE: In order to get this challenge to work properly, you had to remove spaces from the address.
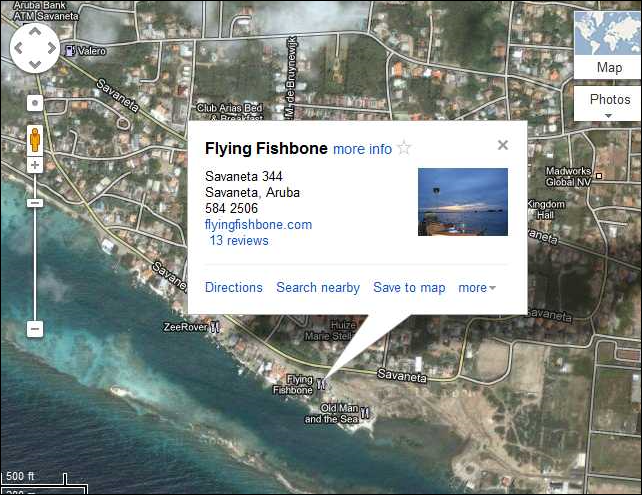
The following image was within the pcap along with an interesting conversation that was had about meeting up in Aruba!
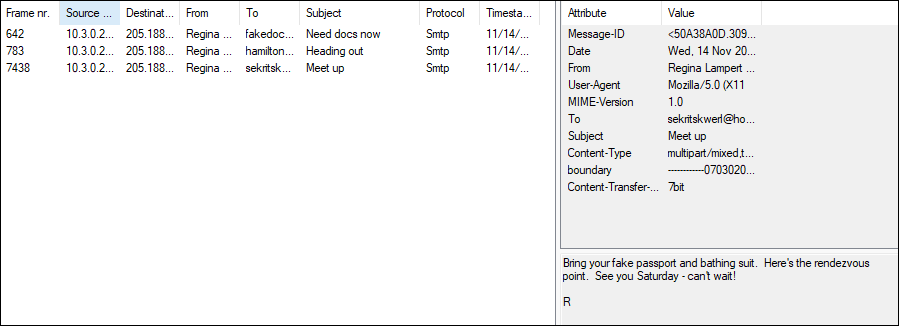
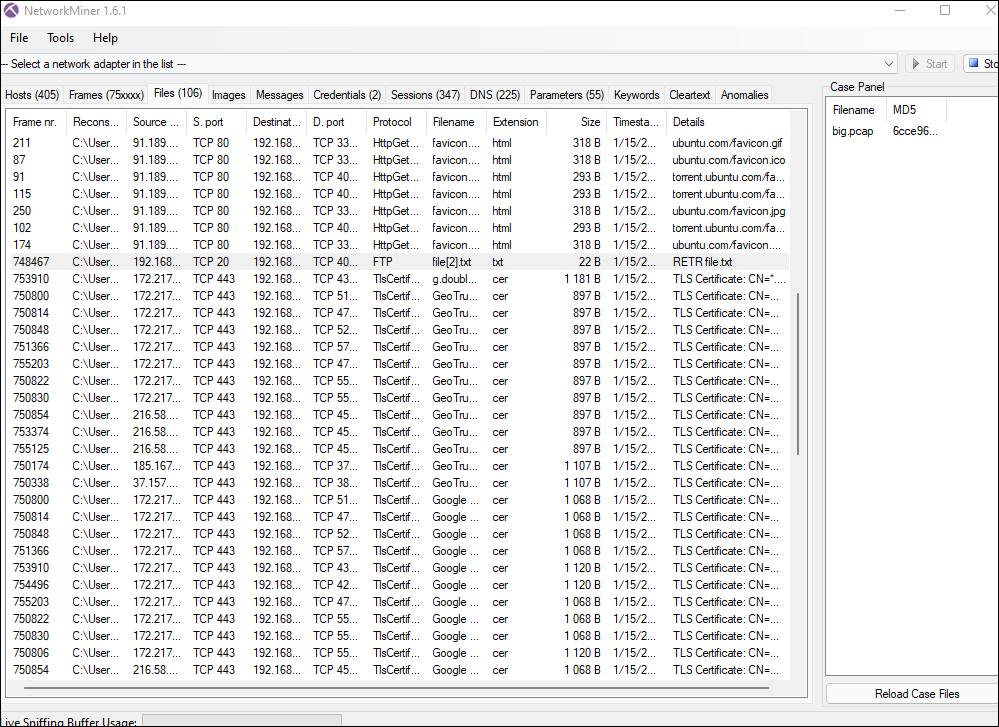
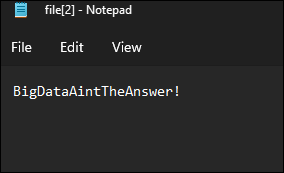
BIG: What's the big deal? You were provided with a 700Mb pcap file to analyze and find a flag in. I definitely used NetworkMiner for this challenge, as the file was huge. I noticed that most of the Protocol and files were certificate related, so I ignored those and quickly zoned in on the one FTP file listed below and opened that file to pull the flag:
WEB
HTTP 2: This HTTP method sends data securely to a server. The answer to this challenge was to simply enter POST as the flag.
Robots.txt: What is Sekrit trying to hide? https://www.sekritskwerl.com
The hint to this challenge lied in its title. In order to see what was being hidden, we went to https://www.sekritskwerl.com/robots.txt to see what was and wasn't allowed:
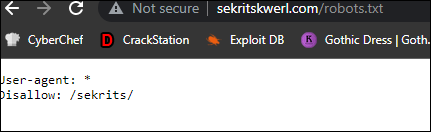
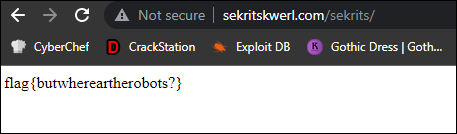
It looked like the path /sekrits/ was disallowed, so I immediately checked the link and found the flag:
Harvest Skwerl: Our old friend Sekrit Skwerl is taking a much needed vacation and posted some photos!
In this challenge, you're provided a link to a bunch of images that Mr. Skwerl took on his vacation.

However, one of these photos was not like the other. After analyzing each photo provided, I went ahead and checked the following image for any sort of steganography that might have shown up and sure enough I found one:

Doing a binwalk check on the file shows that it included a zipped folder, so I went ahead and used the following to extract the contents from the image:
└─$ binwalk -e me-and-missus.jpg
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
0 0x0 JPEG image data, JFIF standard 1.01
1386032 0x152630 Zip archive data, at least v1.0 to extract, compressed size: 24, uncompressed size: 24, name: data
1386192 0x1526D0 End of Zip archive, footer length: 22I was then provided with a zip file, which when extracted, pulled the flag:
Fileviewer: We've been working on a custom file viewer. You only need one page! You just punch in the name of a file you want to see and it'll show it to you! That's what a single page web application is, right? 3 tries.
This challenge was a bit perplexing as I had to go through a lot of trial and error in order to find the answer. You were presented with the following page that seemed to error out and was vulnerable to XSS vulnerabilities, but completely unrelated to the flag (there was a hint provided in the source that told you to ignore the XSS bug):
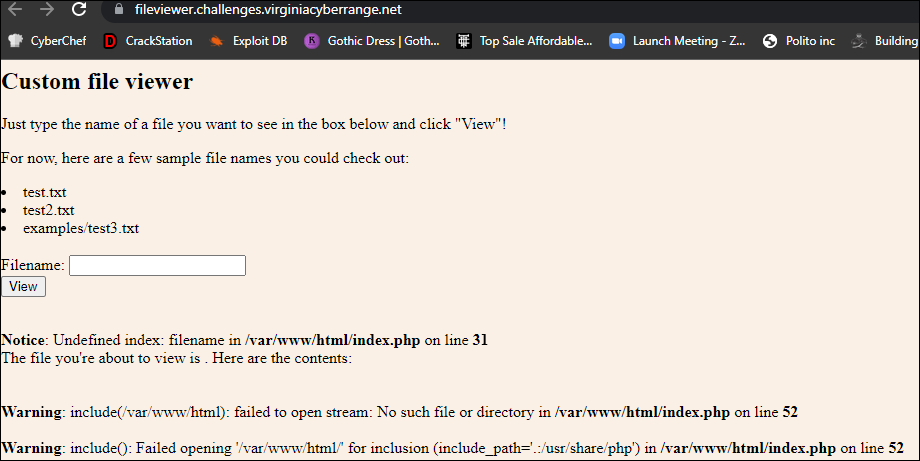
From here, you can enter the following example files and they display below the image. In order to solve this challenge, you had to double encode an LFI statement for /etc/passwd to show. Here is the original LFI found and the result:
%252e%252e%252e%252e//%252e%252e%252e%252e//%252e%252e/%252e%252e%252e%252e//etc/passwd

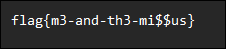
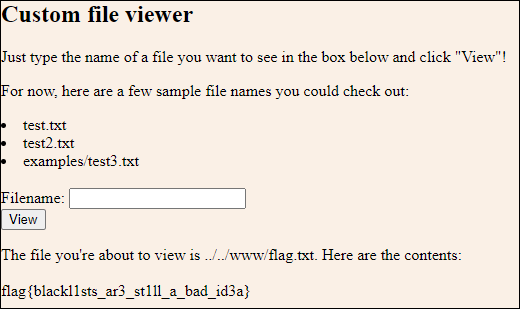
We got an idea of the location of the flag because the errors conveniently provided a little bit of information about the file locations and modifying our LFI, we come up with the following in order to obtain the flag: %252e%252e%252e%252e//%252e%252e/%252e%252e%252e%252e//www/flag.txt
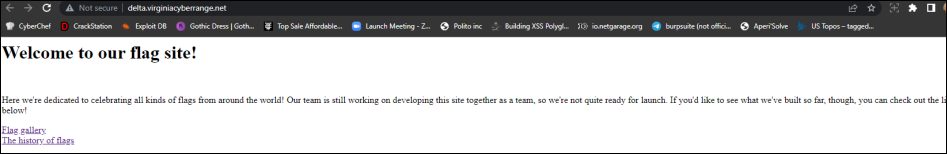
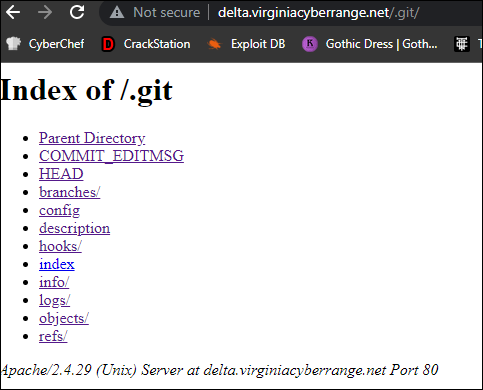
Flags Galore: Git after it! 3 tries.
At first sight you're presented with the following webpage which shows a flag gallery:
Running a dirsearch -u on the site, I was able to quickly enumerate out a /.git/ page that provided information about commits, including the removal of the flag below. However, all of the git information was on the site, so you were able to download the sections provided and combine them to pull the flag.
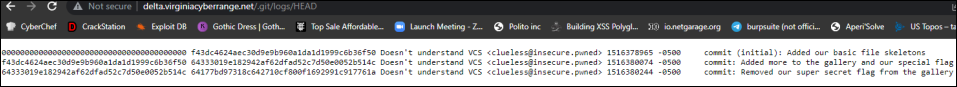
Pulling the commit history provided you with the following information, which included the flag. We unfortunately did not receive this flag cap as when I pasted the flag in, it did not include an underscore (the text below is truncated):
177bd97318c642710cf800f1692991c917761a.xmp:Removed our super secret flag from the gallery
2cdad0a580eaf44490dc408670af378b4d650a.xmp:<h2>Here we've got a glorious collection of flags. Feast your eyes on these magnificent flags from
2cdad0a580eaf44490dc408670af378b4d650a.xmp:around the world! We've even put our own super-special flag in here!</h2>
2cdad0a580eaf44490dc408670af378b4d650a.xmp:<img src="world_flags.png">
2cdad0a580eaf44490dc408670af378b4d650a.xmp:<img src="american-flags.jpg">
2cdad0a580eaf44490dc408670af378b4d650a.xmp:<p>flag{g1t_gud_@_s3cur17y}</p>
333019e182942af62dfad52c7d50e0052b514c.xmp:Added more to the gallery and our special flag
3b762c51abb4096360e45a95943b08168be104.xmp:<p><font color="green">Learn about the history of flags</font></p>
3b762c51abb4096360e45a95943b08168be104.xmp:<p><font color="green">Write about the history of flags</font></p>
3df983f02848784e7c1de75ac0d0b22be3c7b0.xmp:tree 265100644 Flag_of_Great_Britain.svg8>;כ
Y..
100644 american-flags.jpbwYmI7;100644 flag_gallery.html_sjh~V@ 100644 history.htm )I#100644 index.htmlΝ3?:03L��h:100644 world_flags.pngsL$
5ߩ
518d384b8310e0c45281e14659388d48371dcb.xmp:<h2>Here we've got a glorious collection of flags. Feast your eyes on these magnificent flags from
518d384b8310e0c45281e14659388d48371dcb.xmp:around the world! We've even put our own super-special flag in here!</h2>Bravo! The last challenge in the web section provided a website with a login screen and requested that we "login" in order to view the page.
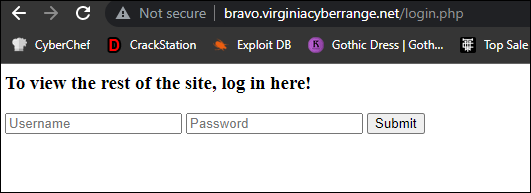
In order to solve this challenge, I viewed the source and browsed around a few directories that came up in dirsearch but came up short.
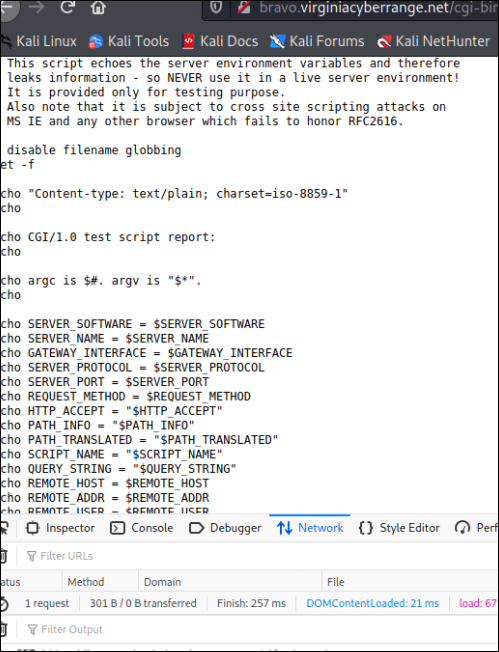
Finally, I checked the site out with curl and changed the name of the base page from login.php to index.php
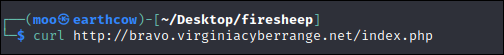
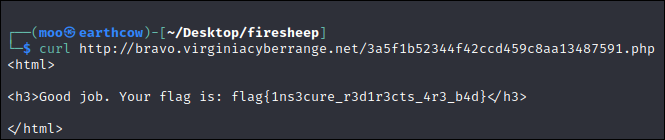
We were then provided with another php subfolder that wasn't anywhere in the source code and curling this link provided the flag in the source file:
REVERSE ENGINEERING
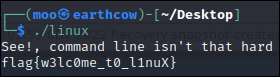
Linux: Run me in Linux
This was pretty cut and dry: Run the program in Linux with ./Linux and pull the flag:
The Bard: That which we call a rose / By any other name would smell as sweet.
This challenge presented you with a file called datafile.txt, but the hint was within the text of the challenge itself. Because the text was obfuscated, I went ahead and popped this in ghidra and noticed some C, so renamed the file to datafile.c
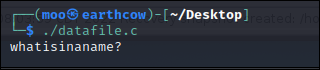
Running ./datafile.c pulled the flag.
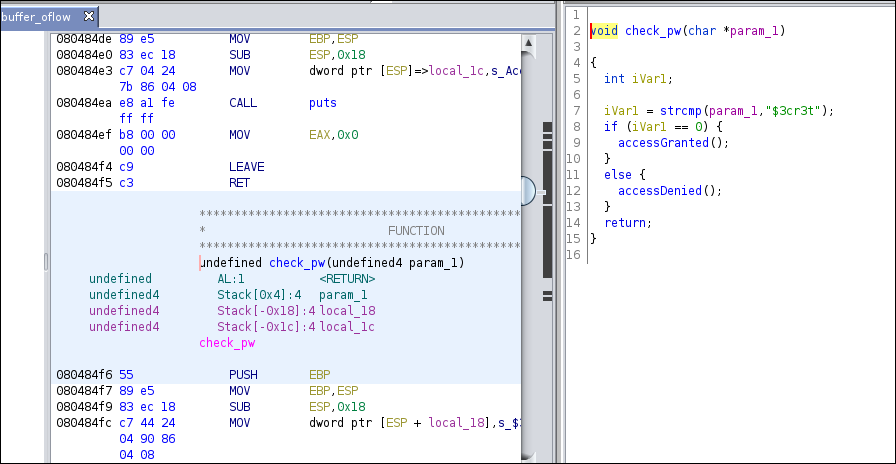
Buffer Overflow 1: Lots of ways to solve this one - one way is using a classic buffer overflow. Can you get the 'accessGranted' function to execute? The flag is the last name of the author quoted.
In order to solve this challenge, I opened the file up in Ghidra and immediately looked for the 'accessGranted' function listed under the functions section on the left hand panel of the program:
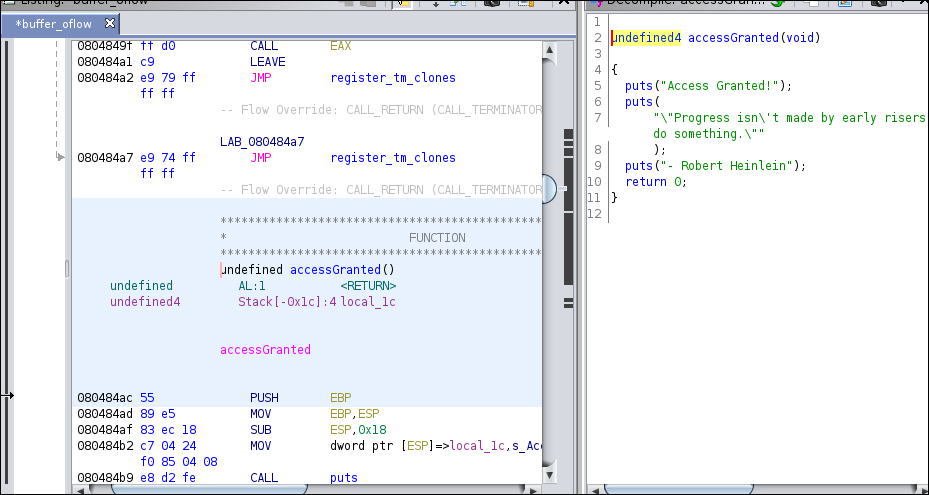
We already have the answer to the flag here, but I went ahead and pulled the password as well, which was $3cr3t then ran the program just to be sure:
┌──(moo㉿earthcow)-[~/Desktop]
└─$ ./buffer_oflow 130 ⨯
Enter password: $3cr3t
Access Granted!
"Progress isn't made by early risers. It's made by lazy men trying to find easier ways to do something."
- Robert HeinleinAs you can guess, the flag was Heinlein.
The Ghost Road: Decrypting the message Juvpu cneg bs n ebnq qb Tubfgf ybir gb geniry gur zbfg? gave you a joke: What's a ghost's favorite kind of road? The answer: A dead end.
Seems Simple: Cheap Windows stego? This challenge consisted of providing the user with a file called streams.rar which was a big tell that the challenge had to deal with using alternate data streams in order to find out more information (you can find more information about this here: https://owasp.org/www-community/attacks/Windows_alternate_data_stream
I went ahead and downloaded Streams on windows then used streams on the filename to pull information. From there, I used the command dir /r and notepad streams.txt:moresekrits.txt in order to pull the flag:
streams v1.60 - Reveal NTFS alternate streams.
Copyright (C) 2005-2016 Mark Russinovich
Sysinternals - www.sysinternals.com
c:\streams.txt:
:moresekrits.txt:$DATA 27
:sekritskwerl.txt:$DATA 23
dir /r
notepad streams.txt:moresekrits.txtREADY PLAYER ..
The last section of the CTF that I'll cover briefly was the Ready Player section that was based on the novel/movie, so most of these questions required a bit of Googling.
One: Who is Kira? Kira is played by Karen Underwood

Two: What is OASIS? A quick Google pulled this up: https://readyplayerone.fandom.com/wiki/OASIS
Three: Who knocked over the comic books: Google again pulls this.
Four: There is a small mailbox here
Five: The elevator called Perzival this: I found the answer to this one on Reddit:
That is the end of our write-up. I had a lot of fun with this CTF and playing with the ladies of Space Cows has been a great joy of mine! I did leave a few challenges out of this write-up as it was relatively long. Still, I hope this was helpful!
Shoutouts to @Faith XY || @MeAsMe || @Lady Acid for being AMAZING!





